Zero Trust Security Market Report Scope & Overview:

Get more information on Zero Trust Security Market - Request Sample Report
The Zero Trust Security Market Size was valued at USD 29.01 Billion in 2023 and is expected to reach USD 117.3 Billion by 2032, growing at a CAGR of 16.8% over the forecast period 2024-2032.
Demand for zero trust security has grown quickly in the past couple of years as cyber threats have gotten more sophisticated and businesses are transiting to remote work or cloud-based system. Zero Trust Security is based on the principle of “never trust; always verify,” requiring all users and devices to authenticate their identity before accessing resources, regardless of their location. Rising Cyberattacks because of the transition to cloud services, increase in remote work and stricter data privacy regulations, this approach is emerging popular among modern societies. Enterprises grew their cybersecurity budgets 12% year over year in 2023, much of which was spent to roll out zero trust security. In fact, 72% of Organizations are already adopting or plan to adopt zero trust security architectures in the next two years according to IDG.
Increasing convergence with Secure Access Service Edge (SASE), As organizations continue to integrate zero trust into their current architecture, implementation of SASE has also increased. Organizations are further adopting capabilities such as AI and machine learning to improve security measures across hybrid cloud infrastructures. Zero trust is becoming a necessity in the face of evolving tactics by cybercriminals to protect valuable information and systems in our digital world. This market growth is attributed to the growing adoption of Bring Your Own Device (BYOD) and Choose Your Own Device (CYOD) trends among enterprises, rising cyber-attacks across industrial sectors, enhanced cybersecurity regulations imposed by governments for public as well as private organizations. Worldwide cyberattacks are up by 28% in 2022 over last year, and the average weekly attacks per organization have exceeded 1,100 globally. By 2024, up to 50% of U.S. employees are working remotely at least part-time, driving the need for Zero Trust Security frameworks to secure remote access and protect corporate networks from breaches.
CYOD/ BYOS, offer benefits like reduced costs in endpoint infrastructure as well provide increased employee productivity by allowing their use of native devices is a pattern that was seen frequently in the COVID-19 pandemic duration while maximum working from home. Zero trust methodologies reinforce security by verifying the endpoint, users and location especially if an organization follows a BYOD model. Attackers are capitalizing on these vulnerabilities as cyber threats heat up, worsening the issues that organizations face and putting important data at risk. Zero trust principles focus on continuously monitoring user behaviour, thereby protecting against financial losses, data breaches, and intellectual property theft. Multi-factor authentication (MFA) adoption is a critical aspect of zero trust security. According to a Microsoft report from 2023, accounts with MFA are 99.9% less likely of getting compromised than those depending only on passwords
Market Dynamics
Drivers
-
Regulations for data protection and information security are becoming more stringent.
-
In SMEs' need for cloud-based zero-trust security solutions is growing.
To secure an individual's data, governments in many nations are focused on the adoption of data protection directives. The surge in sophisticated cyberattacks and the increasing frequency of ransomware attacks on banks and other financial service providers has prompted governments throughout the world to develop a more comprehensive and effective security architecture to protect the information security of business-critical assets. The increased volume of cross-border transactions and data transfers emphasizes the need for data protection and information security rules and regulations that encourage the implementation of zero-trust security solutions by organizations with global footprints. The increasing prevalence of cybercrime has prompted several industries to develop tight data security standards and to continually monitor their networks for potential threats.
Restrains
-
Continuous administration is required to guarantee long-term protection.
To guarantee continuous protection, zero trust security necessitates constant administration. Because organizations, rules, and ongoing operations are always changing, network security needs regular management to guarantee that all activities are secure. Zero-trust security architecture necessitates the use of all security technologies to prevent malicious activity by ensuring that all devices are properly patched and safe. One of the most critical security technologies for a zero-trust security posture is an identity system. Identity systems authenticate a user or device and then verify to the rest of the security tools that the entity is whom it claims to be. The identification of the user or device is used as a point of reference for the policies by the security tools. Identity systems must also be managed on a regular basis in order to secure network endpoints, user databases, and the IT environment.
Segment Analysis
By Security type
The endpoint security segment under the security type held the more than 24% share in 2023. A number of advantages like better patch management, blocking insider threats, web content filtering, and minimizing of AI risks and streamlined cybersecurity. Moreover, vendors operating in the market are introducing improved products to increase their customer base. Apart from this, they are adopting the strategic alternative such as partnerships, acquisition and mergers. For instance, in January 2023, cybersecurity provider Xcitium partnered with communication solution provider Carrier SI. The goal is to provide more “advanced and affordable endpoint protection” with this partnership. Now, Carrier SI customers can be equipped with endpoint cybersecurity that prevents and contain all types of known and unknown cyber-attacks.
The network security segment is likely to grow the highest CAGR during 2024-2032. This trend is driven by key benefits of network security, risk mitigation, safeguarding confidential or proprietary information form insider threats and enabling a digital native experience for customers and workforce. 5G technologies have pushed the network security market businesses to engage in more activities. For example, in January 2023 Trend Micro Incorporated created a new subsidiary, "CTOne", providing end-to-end security of the network for solution 5G. CTOne is designed to improve the digital resilience of vertical application fields and protect landing applications in terms private 5G networks.
By Authentication
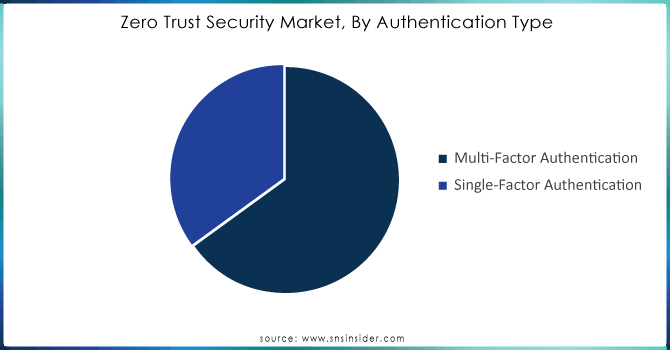
The multi-factor authentication (MFA) dominated the market by accounting for more than 69% share of revenue in 2023, and is anticipated to grow with a significant CAGR during forecast period. Because MFA can offer high-security mechanics of multi-level authorization many industries picked up widespread use. MFA is one of the most important mechanisms in zero-trust, having multiple layers to ensure stringent and continuous verification to gain real-time visibility over access. It may be easier for hackers to hack a single credential, but the presence of multiple verification layers hardens that unauthorized access getting through again aligning with zero-trust security.
Single-factor authentication grow with significant growth rate, which involves verifying users with only one credential such as a password or OTP relies heavily on the strength of the password. A strong password is a mixture of alphabets, cases, figures and special characters because this complexity will make the work harder for hackers to hack your account with their different permutations on these combinations. But many users, unfortunately, fall back on easy-to-remember passwords linked to obvious personal information such as your birthday or name. As a result, the segment is projected to exhibit growth specifically as organizations demand heightened security by way of multi-factor authentication in tandem with single-factor.
Need any customization research on Zero Trust Security Market - Enquiry Now
By Application
IT and telecom led the market in 2023, with a revenue share of more than 45% this segment will continue its dominance over through to forecast period. The increased reliance on cloud-based infrastructure and digital applications for data access, as well as business operations is creating a demand for secure networking solutions that deliver unified access at scale. Also, Telecom service providers who primarily offer data transfer services, are also investing heavily in security technologies. Awareness of zero-trust security's benefits increases, its adoption within this sector is anticipated to rise significantly.
The highest CAGR in the forecast period is being estimated for the healthcare segment between 2024 to 2032. The shifting ground of innovation and technology, notably telehealth services and analytics that improve the connection between end-users and entities alike is necessitating robust network infrastructure services. Moreover, the increase in cyber-attacks on healthcare IT infrastructures has reinforced the call for robust security architectures that shield important data hindered due to cost factor. These attributes are anticipated to boost the necessity of zero-trust security solutions in health IT among businesses, since they wish for protecting sensitive data from both known and unknown cyber hazards.
Regional analysis
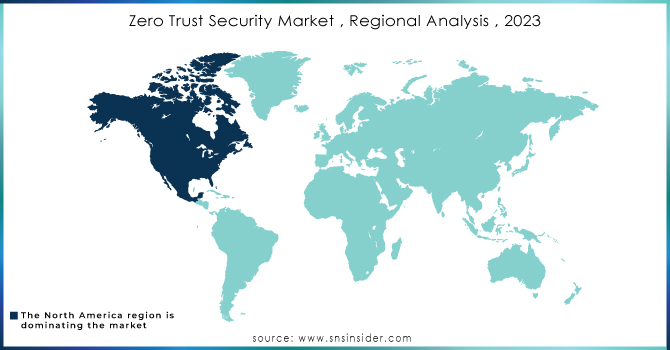
North America accounted for more than 35% revenue share of the global market in 2023, and is projected to expand at a considerable CAGR during the period between 2024 -2032. Growing investments in zero-trust security solutions by government and public authorities are expected to expand the regional market. The increased adoption of IoT, AI and digital technologies by the big enterprises & SMEs along with strict data privacy & security regulations is propelling this growth. Several countries in the North America region such as US and Canada have significantly improved IT infrastructure which gives early access to new advanced technologies for them, this factor provide a competitive advantage over other regions ensures it will continue dominating global zero-trust security Market along with highest market share. One reason businesses are turning to zero trust security solutions is the increase in sophisticated cyberattacks. With sectors such as banking, finance and insurance services (BFSI), government or healthcare relying heavily on IoT devices for digital payments are major consumers of cloud-based applications and largely investing in operation technology the region is only becoming more vulnerable to cyber threats. For instance In January, an attack on Mail Chimp is a classic example of social engineering and it impacted hundreds of its users. There is an urgent requirement of zero-trust policies to stop the escalation and are able to propagate horizontally into networks as these incidents show.
The fastest growth is expected in Asia Pacific during 2024-32. Regional growth is driven by the requirement to secure network against data breaches in public, financial, healthcare and e-commerce sectors. As data breaches continue to occur, the requirement for threat-hunting services has become more apparent. Such as 2 billion voter's private information for sale on the dark web threatening to sell data of other voters around 200 billion in May2020.
Key Players:
The major players are Check Point, Akamai, Microsoft, Palo Alto Networks, Illumio, OKTA, IBM, Cyxtera Technologies, ZScaler, Forcepoint, Google, Trend Micro, Cisco, Broadcom, Trellix, RSA, Centrify, Sophos, Cloudflare, Qnext Corporation, SonicWall, VMware, ON2IT, Fortinet, Varonis, Pulse Secure, and others in the final report.
Recent development
-
Palo Alto Networks released Prisma 3.0 in May of 2024, an evolution of its security platform. Prisma SASE 3.0 also expands Zero Trust to unmanaged devices, helps stop data loss with AI and boost app performance for partners and customers It keeps on conveying best at any point SLA for security handling and application execution. The new capabilities of Prisma SASE 3.0 are expected to be available in the coming months.
-
In May 2024 as well, Palo Alto Networks debuted a collection of new security solutions which were part and parcel designed to AI-enabled threats aimed at enterprises while they also secured designs driven by Artificial Intelligence. Pentagon AI Security developed these solutions with their proprietary technology, Precision AI bringing together machine learning and deep learning powered by Generative Al in real time security.
-
September 2023, Zscaler announced a partnership with CrowdStrike and Imprivata that would provide medical providers with an end to end zero-trust cybersecurity solution This collaboration unifies the ZTS solution of cybersecurity company, Zscaler and Imprivata Digital Identity Platform to deliver better security for a number of medical devices.
| Report Attributes | Details |
| Market Size in 2023 | USD 29.01 Bn |
| Market Size by 2032 | USD 117.3 Bn |
| CAGR | CAGR of 16.8 % From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Offering (Solutions, Services) • By Application (Access Control/ Data Access Control, User Behaviour Analytics (UBA), API Security, Security Analytics, Others) • By Security Type (Network security, Cloud Security, Application Security, Data security, Endpoint security and IoT security) • By Authentication Type (Single-Factor Authentication, Multi-Factor Authentication) • By Vertical (Banking, Financial Services, And Insurance (BFSI), Healthcare Government And Defense, IT & ITES, Retail And E-commerce, Energy And Utilities, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | Check Point, Akamai, Microsoft, Palo Alto Networks, Illumio, OKTA, IBM, Cyxtera Technologies, ZScaler, Forcepoint, Google, Trend Micro, Cisco, Broadcom, Trellix, RSA, Centrify, Sophos, Cloudflare, Qnext Corporation, SonicWall, VMware, ON2IT, Fortinet, Varonis, Pulse Secure |
| Key Drivers | • Regulations for data protection and information security are becoming more stringent. |
| Market Opportunities | • SMEs' need for cloud-based zero-trust security solutions is growing. |

