
Get more information on Serverless Security Market - Request Free Sample Report
The Serverless Security Market size was valued at USD 2.3 billion in 2023 and is expected to reach USD 25.3 billion by 2032, growing at a CAGR of 30.6% over the forecast period of 2024-2032.
The growing adoption of serverless architectures is revolutionizing cloud computing, enabling businesses to focus on code development without managing the underlying infrastructure. This shift has created a robust demand for serverless security solutions. According to the U.S. National Institute of Standards and Technology (NIST) in its 2023 report on cloud service adoption, over 70% of cloud-native applications now leverage serverless models to optimize scalability and reduce operational overhead. The European Commission’s Digital Economy and Society Index (DESI) 2023 indicated that serverless adoption among SMEs in Europe increased by 22% year-on-year, attributed to government incentives promoting cloud transitions under the EU’s Digital Decade Initiative. Additionally, global cybersecurity threats targeting serverless environments surged by 38% in 2023, according to the United Nations’ International Telecommunication Union (ITU). These figures underscore the rising significance of robust serverless security measures to mitigate risks such as function misconfigurations and insecure APIs.
The demand for serverless security solutions has increased, helping organizations protect applications and maintain compliance with industry regulations. In 2023, the European Commission reported that 45.2% of EU enterprises used cloud services, with 75.3% adopting advanced services like database hosting, security software, and development platforms, marking a 4.2% increase from 2021. Additionally, the adoption of DevOps methodologies has led to greater reliance on serverless computing, enabling faster development and deployment cycles. While this enhances agility, it also presents security concerns, including managing identities, detecting vulnerabilities, and ensuring compliance. Consequently, the need for specialized serverless security solutions has grown to help organizations navigate these challenges.
Drivers
Increased reliance on serverless architectures for scalability and cost savings drives demand for specialized security solutions.
The rise in sophisticated cyberattacks against cloud systems fuels the need for tailored serverless security tools to protect against breaches and unauthorized access.
Stringent data protection laws, like GDPR, push organizations to adopt robust security practices in serverless environments to ensure compliance.
The dynamic nature of serverless environments requires continuous monitoring and automated response systems to detect and mitigate potential security risks instantly.
One significant driver of the Serverless Security Market is the growing adoption of serverless computing across industries. As organizations increasingly migrate their applications to serverless architectures, they benefit from enhanced scalability, reduced operational costs, and simplified infrastructure management. Serverless platforms, such as AWS Lambda and Azure Functions, enable developers to deploy applications without managing the underlying servers, allowing them to focus on writing code instead of dealing with infrastructure. For instance, Amazon Web Services (AWS) reported in 2023 that its Lambda service has supported over 400 billion executions monthly, highlighting the scale of serverless adoption. Similarly, companies like Coca-Cola and Capital One have adopted serverless computing to improve operational efficiency and reduce the overhead of managing traditional server-based infrastructures.
However, as organizations embrace these benefits, they also face new security challenges. Serverless environments introduce complexities such as the ephemeral nature of serverless functions, which can be difficult to monitor for potential security risks. As a result, specialized security solutions are critical to protect these dynamic systems from vulnerabilities like unauthorized access and data breaches. This driver is further reinforced by the increasing need for organizations to ensure their cloud environments remain secure as they transition to serverless models.
Restraints
Serverless computing's abstracted infrastructure makes it challenging to gain visibility into network traffic and application behavior, hindering security monitoring.
Serverless systems automatically scale with demand, creating unpredictable security challenges and complicating efforts to maintain consistent protection.
The lack of visibility in serverless environments is an important obstacle in the Serverless Security market. Since serverless computing abstracts away much of the underlying infrastructure, it becomes challenging for security teams to monitor application behavior and network traffic effectively. The absence of transparency creates a challenge in identifying vulnerabilities or unusual activities that could be suggestive of a breach. Security teams have visibility into and control over systems in traditional server environments, but much of that is hidden in cloud provider architecture, such as with serverless computing. This results in a complicated detection of dangers in real-time preventing fast response and leading to a higher probability of data breaches or other cyberattacks. Furthermore, as serverless applications scale dynamically, security teams may struggle to keep up with new functions being created and the continuously changing environment.
By Service Model
In 2023, the function as a service (FaaS) segment accounted for 68% of the global serverless security market revenue. FaaS is already dominating this segment because it allows developers to run and scale specific functions of code without provisioning servers. The 2023 Technology Adoption Report published by the Government of Canada indicates that 85% of public sector cloud deployments incorporated FaaS for its price advantage and ease of use. Likewise, the U.K. Government Digital Transformation Plan demonstrated that 60% of gov-backed tech startups that used FaaS found it useful to deploy in an agile manner. Combined with the increasing popularity of FaaS in sectors like healthcare and e-commerce, where scalability and cost-effectiveness are key performance indicators, makes it the way ahead. This growth is in step with global initiatives to simplify and accelerate cloud-native application development through easier, serverless methods.

Do you need any custom research/data on Serverless Security Market - Enquiry Now
By Security Type
Application security was the leading category by security type, capturing 30% of global revenue in 2023. This segment is expected to continue to dominate the market due to the growing need for securing serverless applications against various threats, like injection attacks, cross-site scripting (XSS), and unauthorized access. The U.K. National Cyber Security Centre (NCSC) reported in 2023 that serverless application vulnerabilities comprise 45% of all reported issues. At the same time, U.S. Cybersecurity and Infrastructure Security Agency (CISA) has urged the need for improved application secureness paradigms for serverless models owing to risks of exploitation via APIs. Owing to stricter compliance mandates imposed globally, there was an increase in adoption of Application Security solutions across serverless architectures.
By End Use
The segment of IT & telecommunications dominated the market in 2023, with 22% of global revenue share. This dominance in the sector is indicative of the rise in serverless computing that the sector has experienced as a means of improving scalability and operational efficiency. According to the U.S. Federal Communications Commission (FCC), more than half of U.S. telecom operators made the shift to serverless models in 2023, to increase infrastructure resilience and decrease latency. Moreover, 40% of IT companies had integrated serverless frameworks under the Digital India initiative by the Indian Ministry of Electronics and Information Technology (MeitY). The growing IT and Telecom sector in response to the combination of rising data traffic and cloud migration strategies has significantly upsurged the demand for effective serverless security solutions.
By Enterprise Size
Large enterprises dominated the market with 62% revenue share in 2023. Due to the extent of their application portfolios and greater risk from advanced cyber threats, large corporations are often at the forefront of serverless security adoption. In a 2023 report by the Australian Cyber Security Centre [ACSC], 75% of enterprises highlighted their serverless security investments to save from growing threats. Similarly, the U.S. Department of Commerce also cautioned against cyber threats leading to Fortune 500 companies increasing their spending on serverless-related applications by 18 percent in 2023 as the sector continued to depend on strengthened security frameworks for compliance and risk management. This trend was further propelled by government incentives promoting the adoption of secure cloud environments for large enterprises.
North America led the global serverless security market and accounted for 38% revenue share in 2023. Investments in cloud infrastructure and strict regulations in cybersecurity come as enablers for regional leadership. The U.S. Bureau of Economic Analysis has reported ever-growing federal and private sector spending on serverless security solutions growing significantly year-on-year. The increasing adoption of cloud-native architectures is expected to drive rapid growth in the U.S. serverless security market from 2024 to 2032. Finally, with organizations migrating their workloads from legacy infrastructure to serverless computing to support their efforts for scalability and flexibility, they need more advanced security solutions to secure the serverless environment which requires more investment in both in-house and outside sources.
On the other hand, Asia-Pacific showed the highest CAGR over the forecast period due to the ongoing digital transformation in emerging economies like India and Indonesia. According to the 2023 report on the Digital India progress, the Indian government indicated that serverless deployments grew by 30%, and specifically mentions the public and private sectors engaged in the Indian Smart Cities Mission. This trend is further complemented by high mobile adoption and an emergent demand for cloud technologies across the region.

In May 2024: StackHawk Partnered with Microsoft Defender for Cloud to advance secure software development. It enhances Defender for APIs' runtime capabilities by adding the integration for more robust visibility into API security during development, as well as for security teams.
In March 2023, The U.S. Department of Homeland Security (DHS) announced a $200 million grant for developing advanced serverless security technologies, focusing on protecting federal cloud systems.
Service Providers / Manufacturers
StackHawk (StackHawk API Security, StackHawk Web Application Security)
Microsoft (Defender for Cloud, Defender for APIs)
McAfee (McAfee Cloud Security, McAfee Data Loss Prevention)
Palo Alto Networks (Prisma Cloud, Prisma Cloud Compute)
Trend Micro (Cloud One, Deep Security)
Fortinet (FortiWeb, FortiGate Cloud)
Check Point Software (CloudGuard, ThreatCloud)
Cloudflare (Cloudflare Workers, Cloudflare Security)
Zscaler (Zscaler Cloud Security, Zscaler Private Access)
IBM (IBM Cloud Security, IBM QRadar)
Key Users
Netflix
Amazon
Microsoft Azure
Uber
Spotify
Walmart
Dropbox
Airbnb
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 2.3 billion |
| Market Size by 2032 | USD 25.3 billion |
| CAGR | CAGR 30.6% from 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Service Model (Function as a Service, Backend as a Service) • By Deployment (Cloud, On-Premise) • By Security Type (Data Security, Network Security, Application Security, Perimeter Security, Others) • By Enterprise Size (SMEs, Large Enterprises) • By End Use (BFSI, Healthcare, Retail and E-commerce, IT and Telecommunications, Government and Public Sector, Manufacturing, Energy and Utilities, Others) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | StackHawk, Microsoft, McAfee, Palo Alto Networks, Trend Micro, Fortinet, Check Point Software, Cloudflare, Zscaler, IBM |
| Key Drivers | • Increased reliance on serverless architectures for scalability and cost savings drives demand for specialized security solutions. • The rise in sophisticated cyberattacks against cloud systems fuels the need for tailored serverless security tools to protect against breaches and unauthorized access. • Stringent data protection laws, like GDPR, push organizations to adopt robust security practices in serverless environments to ensure compliance. • The dynamic nature of serverless environments requires continuous monitoring and automated response systems to detect and mitigate potential security risks instantly. |
| Market Restraints | • Serverless computing's abstracted infrastructure makes it challenging to gain visibility into network traffic and application behavior, hindering security monitoring. • Serverless systems automatically scale with demand, creating unpredictable security challenges and complicating efforts to maintain consistent protection. |
Ans: The Serverless Security Market is projected to reach USD 25.3 billion by 2032.
Ans: The Serverless Security Market is expected to grow at a CAGR of 30.6% during the forecast period of 2024-2032.
Ans: Some of the major key players in the Serverless Security Market are StackHawk, Microsoft, McAfee, Palo Alto Networks, Trend Micro, Fortinet, Check Point Software, Cloudflare, Zscaler, IBM, among others.
Ans: North America dominates the Serverless Security Market.
Ans: Some of the major growth drivers of the Serverless Security Market are:
Increased reliance on serverless architectures for scalability and cost savings drives demand for specialized security solutions?.
The rise in sophisticated cyberattacks against cloud systems fuels the need for tailored serverless security tools to protect against breaches and unauthorized access?.
Table of Contents:
1. Introduction
1.1 Market Definition
1.2 Scope (Inclusion and Exclusions)
1.3 Research Assumptions
2. Executive Summary
2.1 Market Overview
2.2 Regional Synopsis
2.3 Competitive Summary
3. Research Methodology
3.1 Top-Down Approach
3.2 Bottom-up Approach
3.3. Data Validation
3.4 Primary Interviews
4. Market Dynamics Impact Analysis
4.1 Market Driving Factors Analysis
4.1.1 Drivers
4.1.2 Restraints
4.1.3 Opportunities
4.1.4 Challenges
4.2 PESTLE Analysis
4.3 Porter’s Five Forces Model
5. Statistical Insights and Trends Reporting
5.1 Cybersecurity Threat Landscape in Serverless Environments (2023)
5.2 User Demographics and Adoption by Industry (2023)
5.3 Integration Capabilities with Cloud Platforms (2023)
5.4 Impact of Serverless Security on Compliance and Governance (2023)
5.5 Emerging Technologies and Innovation in Serverless Security (2023)
6. Competitive Landscape
6.1 List of Major Companies, By Region
6.2 Market Share Analysis, By Region
6.3 Product Benchmarking
6.3.1 Product specifications and features
6.3.2 Pricing
6.4 Strategic Initiatives
6.4.1 Marketing and promotional activities
6.4.2 Distribution and supply chain strategies
6.4.3 Expansion plans and new product launches
6.4.4 Strategic partnerships and collaborations
6.5 Technological Advancements
6.6 Market Positioning and Branding
7. Serverless Security Market Segmentation, By Service Model
7.1 Chapter Overview
7.2 Function as a Service (FaaS)
7.2.1 Function as a Service (FaaS) Market Trends Analysis (2020-2032)
7.2.2 Function as a Service (FaaS) Market Size Estimates And Forecasts To 2032 (USD Billion)
7.3 Backend as a Service (BaaS)
7.3.1 Backend as a Service (BaaS) Market Trends Analysis (2020-2032)
7.3.2 Backend as a Service (BaaS) Deposition Market Size Estimates And Forecasts To 2032 (USD Billion)
8. Serverless Security Market Segmentation, By Enterprise Size
8.1 Chapter Overview
8.2 Small & Medium Enterprises
8.2.1 Small & Medium Enterprises Market Trends Analysis (2020-2032)
8.2.2 Small & Medium Enterprises Market Size Estimates And Forecasts To 2032 (USD Billion)
8.3 Large Enterprises
8.3.1 Large Enterprises Market Trends Analysis (2020-2032)
8.3.2 Large Enterprises Market Size Estimates And Forecasts To 2032 (USD Billion)
9. Serverless Security Market Segmentation, By Deployment
9.1 Chapter Overview
9.2 Cloud
9.2.1 Cloud Market Trends Analysis (2020-2032)
9.2.2 Cloud Market Size Estimates And Forecasts To 2032 (USD Billion)
9.3 On-Premise
9.3.1 On-Premise Market Trends Analysis (2020-2032)
9.3.2 On-Premise Market Size Estimates And Forecasts To 2032 (USD Billion)
10. Serverless Security Market Segmentation, By Security Type
10.1 Chapter Overview
10.2 Data Security
10.2.1 Data Security Market Trends Analysis (2020-2032)
10.2.2 Data Security Market Size Estimates And Forecasts To 2032 (USD Billion)
10.3 Network Security
10.3.1 Network Security Market Trends Analysis (2020-2032)
10.3.2 Network Security Market Size Estimates And Forecasts To 2032 (USD Billion)
10.4 Application Security
10.4.1 Application Security Market Trends Analysis (2020-2032)
10.4.2 Application Security Market Size Estimates And Forecasts To 2032 (USD Billion)
10.5 Perimeter Security
10.5.1 Perimeter Security Market Trends Analysis (2020-2032)
10.5.2 Perimeter Security Deposition Market Size Estimates And Forecasts To 2032 (USD Billion)
10.6 Others
10.6.1 Others Market Trends Analysis (2020-2032)
10.6.2 Others Deposition Market Size Estimates And Forecasts To 2032 (USD Billion)
11. Serverless Security Market Segmentation, By End-use
11.1 Chapter Overview
11.2 BFSI
11.2.1 BFSI Market Trends Analysis (2020-2032)
11.2.2 BFSI Market Size Estimates And Forecasts To 2032 (USD Billion)
11.3 Retail and E-commerce
11.3.1 Retail and E-commerce Market Trends Analysis (2020-2032)
11.3.2 Retail and E-commerce Market Size Estimates And Forecasts To 2032 (USD Billion)
11.4 Healthcare
11.4.1 Healthcare Market Trends Analysis (2020-2032)
11.4.2 Healthcare Market Size Estimates And Forecasts To 2032 (USD Billion)
11.5 IT and Telecommunications
11.5.1 IT and Telecommunications Market Trends Analysis (2020-2032)
11.5.2 IT and Telecommunications Market Size Estimates And Forecasts To 2032 (USD Billion)
11.6 Government and Public Sector
11.6.1 Government and Public Sector Market Trends Analysis (2020-2032)
11.6.2 Government and Public Sector Market Size Estimates And Forecasts To 2032 (USD Billion)
11.7 Manufacturing
11.7.1 Manufacturing Market Trends Analysis (2020-2032)
11.7.2 Manufacturing Market Size Estimates And Forecasts To 2032 (USD Billion)
11.8 Energy and Utilities
11.8.1 Energy and Utilities Market Trends Analysis (2020-2032)
11.8.2 Energy and Utilities Market Size Estimates And Forecasts To 2032 (USD Billion)
11.9 Others
11.9.1 Others Market Trends Analysis (2020-2032)
11.9.2 Others Market Size Estimates And Forecasts To 2032 (USD Billion)
12. Regional Analysis
12.1 Chapter Overview
12.2 North America
12.2.1 Trends Analysis
12.2.2 North America Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.2.3 North America Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.2.4 North America Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.5 North America Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.6 North America Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.7 North America Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.2.8 USA
12.2.8.1 USA Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.2.8.2 USA Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.8.3 USA Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.8.4 USA Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.8.5 USA Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.2.9 Canada
12.2.9.1 Canada Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.2.9.2 Canada Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.9.3 Canada Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.9.4 Canada Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.9.5 Canada Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.2.10 Mexico
12.2.10.1 Mexico Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.2.10.2 Mexico Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.10.3 Mexico Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.10.4 Mexico Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.10.5 Mexico Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3 Europe
12.3.1 Eastern Europe
12.3.1.1 Trends Analysis
12.3.1.2 Eastern Europe Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.3.1.3 Eastern Europe Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.1.4 Eastern Europe Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.5 Eastern Europe Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.6 Eastern Europe Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.7 Eastern Europe Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.1.8 Poland
12.3.1.8.1 Poland Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.1.8.2 Poland Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.8.3 Poland Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.8.4 Poland Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.8.5 Poland Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.1.9 Romania
12.3.1.9.1 Romania Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.1.9.2 Romania Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.9.3 Romania Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.9.4 Romania Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.9.5 Romania Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.1.10 Hungary
12.3.1.10.1 Hungary Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.1.10.2 Hungary Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.10.3 Hungary Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.10.4 Hungary Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.10.5 Hungary Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.1.11 Turkey
12.3.1.11.1 Turkey Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.1.11.2 Turkey Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.11.3 Turkey Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.11.4 Turkey Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.11.5 Turkey Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.1.12 Rest Of Eastern Europe
12.3.1.12.1 Rest Of Eastern Europe Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.1.12.2 Rest Of Eastern Europe Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.12.3 Rest Of Eastern Europe Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.12.4 Rest Of Eastern Europe Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.12.5 Rest Of Eastern Europe Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2 Western Europe
12.3.2.1 Trends Analysis
12.3.2.2 Western Europe Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.3.2.3 Western Europe Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.4 Western Europe Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.5 Western Europe Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.6 Western Europe Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.7 Western Europe Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.8 Germany
12.3.2.8.1 Germany Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.8.2 Germany Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.8.3 Germany Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.8.4 Germany Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.8.5 Germany Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.9 France
12.3.2.9.1 France Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.9.2 France Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.9.3 France Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.9.4 France Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.9.5 France Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.10 UK
12.3.2.10.1 UK Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.10.2 UK Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.10.3 UK Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.10.4 UK Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.10.5 UK Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.11 Italy
12.3.2.11.1 Italy Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.11.2 Italy Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.11.3 Italy Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.11.4 Italy Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.11.5 Italy Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.12 Spain
12.3.2.12.1 Spain Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.12.2 Spain Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.12.3 Spain Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.12.4 Spain Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.12.5 Spain Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.13 Netherlands
12.3.2.13.1 Netherlands Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.13.2 Netherlands Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.13.3 Netherlands Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.13.4 Netherlands Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.13.5 Netherlands Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.14 Switzerland
12.3.2.14.1 Switzerland Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.14.2 Switzerland Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.14.3 Switzerland Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.14.4 Switzerland Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.12.5 Switzerland Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.15 Austria
12.3.2.15.1 Austria Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.15.2 Austria Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.15.3 Austria Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.15.4 Austria Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.15.5 Austria Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.3.2.16 Rest Of Western Europe
12.3.2.16.1 Rest Of Western Europe Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.3.2.16.2 Rest Of Western Europe Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.16.3 Rest Of Western Europe Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.16.4 Rest Of Western Europe Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.16.5 Rest Of Western Europe Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4 Asia Pacific
12.4.1 Trends Analysis
12.4.2 Asia Pacific Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.4.3 Asia Pacific Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.4 Asia Pacific Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.5 Asia Pacific Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.6 Asia Pacific Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.7 Asia Pacific Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.8 China
12.4.8.1 China Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.8.2 China Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.8.3 China Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.8.4 China Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.8.5 China Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.9 India
12.4.9.1 India Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.9.2 India Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.9.3 India Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.9.4 India Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.9.5 India Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.10 Japan
12.4.10.1 Japan Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.10.2 Japan Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.10.3 Japan Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.10.4 Japan Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.10.5 Japan Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.11 South Korea
12.4.11.1 South Korea Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.11.2 South Korea Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.11.3 South Korea Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.11.4 South Korea Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.11.5 South Korea Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.12 Vietnam
12.4.12.1 Vietnam Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.12.2 Vietnam Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.12.3 Vietnam Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.12.4 Vietnam Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.12.5 Vietnam Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.13 Singapore
12.4.13.1 Singapore Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.13.2 Singapore Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.13.3 Singapore Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.13.4 Singapore Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.13.5 Singapore Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.14 Australia
12.4.14.1 Australia Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.14.2 Australia Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.14.3 Australia Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.14.4 Australia Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.14.5 Australia Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.4.15 Rest Of Asia Pacific
12.4.15.1 Rest Of Asia Pacific Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.4.15.2 Rest Of Asia Pacific Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.15.3 Rest Of Asia Pacific Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.15.4 Rest Of Asia Pacific Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.15.5 Rest Of Asia Pacific Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5 Middle East And Africa
12.5.1 Middle East
12.5.1.1 Trends Analysis
12.5.1.2 Middle East Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.5.1.3 Middle East Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.1.4 Middle East Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.5 Middle East Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.6 Middle East Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.7 Middle East Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.1.8 UAE
12.5.1.8.1 UAE Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.1.8.2 UAE Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.8.3 UAE Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.8.4 UAE Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.8.5 UAE Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.1.9 Egypt
12.5.1.9.1 Egypt Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.1.9.2 Egypt Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.9.3 Egypt Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.9.4 Egypt Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.9.5 Egypt Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.1.10 Saudi Arabia
12.5.1.10.1 Saudi Arabia Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.1.10.2 Saudi Arabia Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.10.3 Saudi Arabia Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.10.4 Saudi Arabia Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.10.5 Saudi Arabia Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.1.11 Qatar
12.5.1.11.1 Qatar Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.1.11.2 Qatar Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.11.3 Qatar Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.11.4 Qatar Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.11.5 Qatar Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.1.12 Rest Of Middle East
12.5.1.12.1 Rest Of Middle East Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.1.12.2 Rest Of Middle East Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.12.3 Rest Of Middle East Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.12.4 Rest Of Middle East Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.12.5 Rest Of Middle East Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.2 Africa
12.5.2.1 Trends Analysis
12.5.2.2 Africa Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.5.2.3 Africa Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.2.4 Africa Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.5 Africa Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.6 Africa Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.7 Africa Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.2.8 South Africa
12.5.2.8.1 South Africa Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.2.8.2 South Africa Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.8.3 South Africa Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.8.4 South Africa Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.8.5 South Africa Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.2.9 Nigeria
12.5.2.9.1 Nigeria Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.2.9.2 Nigeria Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.9.3 Nigeria Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.9.4 Nigeria Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.9.5 Nigeria Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.5.2.10 Rest Of Africa
12.5.2.10.1 Rest Of Africa Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.5.2.10.2 Rest Of Africa Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.10.3 Rest Of Africa Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.10.4 Rest Of Africa Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.10.5 Rest Of Africa Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.6 Latin America
12.6.1 Trends Analysis
12.6.2 Latin America Serverless Security Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.6.3 Latin America Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.6.4 Latin America Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.5 Latin America Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.6 Latin America Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.7 Latin America Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.6.8 Brazil
12.6.8.1 Brazil Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.6.8.2 Brazil Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.8.3 Brazil Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.8.4 Brazil Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.8.5 Brazil Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.6.9 Argentina
12.6.9.1 Argentina Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.6.9.2 Argentina Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.9.3 Argentina Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.9.4 Argentina Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.9.5 Argentina Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.6.10 Colombia
12.6.10.1 Colombia Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.6.10.2 Colombia Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.10.3 Colombia Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.10.4 Colombia Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.10.5 Colombia Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
12.6.11 Rest Of Latin America
12.6.11.1 Rest Of Latin America Serverless Security Market Estimates And Forecasts, By Service Model (2020-2032) (USD Billion)
12.6.11.2 Rest Of Latin America Serverless Security Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.11.3 Rest Of Latin America Serverless Security Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.11.4 Rest Of Latin America Serverless Security Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.11.5 Rest Of Latin America Serverless Security Market Estimates And Forecasts, By End-use (2020-2032) (USD Billion)
13. Company Profiles
13.1 StackHawk
13.1.1 Company Overview
13.1.2 Financial
13.1.3 Products/ Services Offered
13.1.4 SWOT Analysis
13.2 Microsoft
13.2.1 Company Overview
13.2.2 Financial
13.2.3 Products/ Services Offered
13.2.4 SWOT Analysis
13.3 McAfee
13.3.1 Company Overview
13.3.2 Financial
13.3.3 Products/ Services Offered
13.3.4 SWOT Analysis
13.4 Palo Alto Networks
13.4.1 Company Overview
13.4.2 Financial
13.4.3 Products/ Services Offered
13.4.4 SWOT Analysis
13.5 Trend Micro
13.5.1 Company Overview
13.5.2 Financial
13.5.3 Products/ Services Offered
13.5.4 SWOT Analysis
13.6 Fortinet
13.6.1 Company Overview
13.6.2 Financial
13.6.3 Products/ Services Offered
13.6.4 SWOT Analysis
13.7 Check Point Software
13.7.1 Company Overview
13.7.2 Financial
13.7.3 Products/ Services Offered
13.10.5 SWOT Analysis
13.8 Cloudflare
13.8.1 Company Overview
13.8.2 Financial
13.8.3 Products/ Services Offered
13.8.4 SWOT Analysis
13.9 Zscaler
13.9.1 Company Overview
13.9.2 Financial
13.9.3 Products/ Services Offered
13.9.4 SWOT Analysis
13.10 IBM
13.12.1 Company Overview
13.12.2 Financial
13.12.3 Products/ Services Offered
13.12.4 SWOT Analysis
14. Use Cases and Best Practices
15. Conclusion
An accurate research report requires proper strategizing as well as implementation. There are multiple factors involved in the completion of good and accurate research report and selecting the best methodology to compete the research is the toughest part. Since the research reports we provide play a crucial role in any company’s decision-making process, therefore we at SNS Insider always believe that we should choose the best method which gives us results closer to reality. This allows us to reach at a stage wherein we can provide our clients best and accurate investment to output ratio.
Each report that we prepare takes a timeframe of 350-400 business hours for production. Starting from the selection of titles through a couple of in-depth brain storming session to the final QC process before uploading our titles on our website we dedicate around 350 working hours. The titles are selected based on their current market cap and the foreseen CAGR and growth.
The 5 steps process:
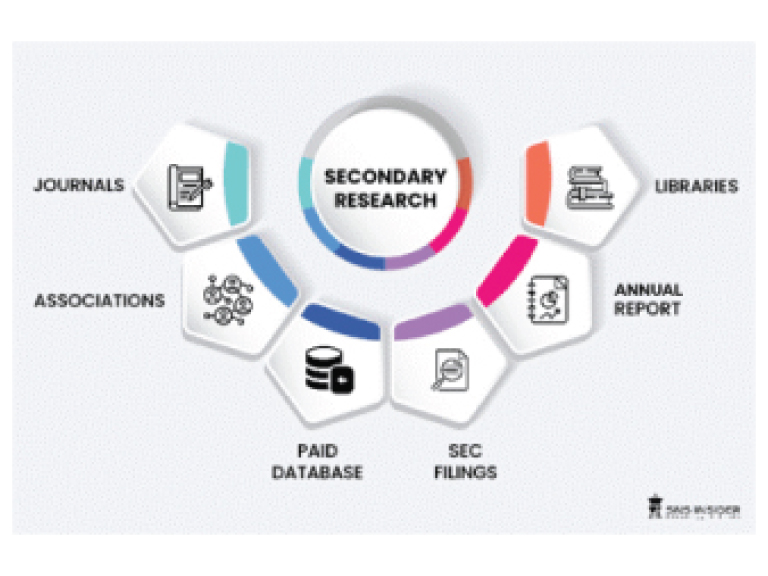
Step 1: Secondary Research:
Secondary Research or Desk Research is as the name suggests is a research process wherein, we collect data through the readily available information. In this process we use various paid and unpaid databases which our team has access to and gather data through the same. This includes examining of listed companies’ annual reports, Journals, SEC filling etc. Apart from this our team has access to various associations across the globe across different industries. Lastly, we have exchange relationships with various university as well as individual libraries.
Step 2: Primary Research
When we talk about primary research, it is a type of study in which the researchers collect relevant data samples directly, rather than relying on previously collected data. This type of research is focused on gaining content specific facts that can be sued to solve specific problems. Since the collected data is fresh and first hand therefore it makes the study more accurate and genuine.
We at SNS Insider have divided Primary Research into 2 parts.
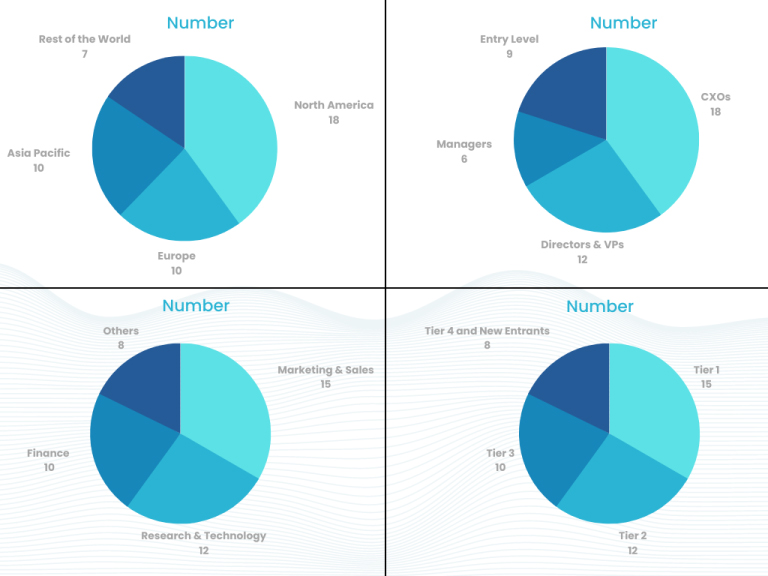
Part 1 wherein we interview the KOLs of major players as well as the upcoming ones across various geographic regions. This allows us to have their view over the market scenario and acts as an important tool to come closer to the accurate market numbers. As many as 45 paid and unpaid primary interviews are taken from both the demand and supply side of the industry to make sure we land at an accurate judgement and analysis of the market.
This step involves the triangulation of data wherein our team analyses the interview transcripts, online survey responses and observation of on filed participants. The below mentioned chart should give a better understanding of the part 1 of the primary interview.
Part 2: In this part of primary research the data collected via secondary research and the part 1 of the primary research is validated with the interviews from individual consultants and subject matter experts.
Consultants are those set of people who have at least 12 years of experience and expertise within the industry whereas Subject Matter Experts are those with at least 15 years of experience behind their back within the same space. The data with the help of two main processes i.e., FGDs (Focused Group Discussions) and IDs (Individual Discussions). This gives us a 3rd party nonbiased primary view of the market scenario making it a more dependable one while collation of the data pointers.
Step 3: Data Bank Validation
Once all the information is collected via primary and secondary sources, we run that information for data validation. At our intelligence centre our research heads track a lot of information related to the market which includes the quarterly reports, the daily stock prices, and other relevant information. Our data bank server gets updated every fortnight and that is how the information which we collected using our primary and secondary information is revalidated in real time.

Step 4: QA/QC Process
After all the data collection and validation our team does a final level of quality check and quality assurance to get rid of any unwanted or undesired mistakes. This might include but not limited to getting rid of the any typos, duplication of numbers or missing of any important information. The people involved in this process include technical content writers, research heads and graphics people. Once this process is completed the title gets uploader on our platform for our clients to read it.
Step 5: Final QC/QA Process:
This is the last process and comes when the client has ordered the study. In this process a final QA/QC is done before the study is emailed to the client. Since we believe in giving our clients a good experience of our research studies, therefore, to make sure that we do not lack at our end in any way humanly possible we do a final round of quality check and then dispatch the study to the client.
Key Segments:
By Service Model
Function as a Service (FaaS)
Backend as a Service (BaaS)
By Deployment
Cloud
On-Premise
By Security Type
Data Security
Network Security
Application Security
Perimeter Security
Others
By Enterprise Size
SMEs
Large Enterprises
By End Use
BFSI
Healthcare
Retail and E-commerce
IT and Telecommunications
Government and Public Sector
Manufacturing
Energy and Utilities
Others
Request for Segment Customization as per your Business Requirement: Segment Customization Request
REGIONAL COVERAGE:
North America
US
Canada
Mexico
Europe
Eastern Europe
Poland
Romania
Hungary
Turkey
Rest of Eastern Europe
Western Europe
Germany
France
UK
Italy
Spain
Netherlands
Switzerland
Austria
Rest of Western Europe
Asia Pacific
China
India
Japan
South Korea
Vietnam
Singapore
Australia
Rest of Asia Pacific
Middle East & Africa
Middle East
UAE
Egypt
Saudi Arabia
Qatar
Rest of the Middle East
Africa
Nigeria
South Africa
Rest of Africa
Latin America
Brazil
Argentina
Colombia
Rest of Latin America
Request for Country Level Research Report: Country Level Customization Request
Available Customization
With the given market data, SNS Insider offers customization as per the company’s specific needs. The following customization options are available for the report:
Product Analysis
Criss-Cross segment analysis (e.g. Product X Application)
Product Matrix which gives a detailed comparison of product portfolio of each company
Geographic Analysis
Additional countries in any of the regions
Company Information
Detailed analysis and profiling of additional market players (Up to five)
The Passwordless Authentication Market size was valued at USD 17.1 billion in 2024 and will grow to USD 71.2 billion by 2032 and grow at a CAGR of 17.2 % by 2032.
The Oil and Gas Data Management Market was valued at USD 26.9 billion in 2023 and is expected to reach USD 91.4 billion by 2032, growing at a CAGR of 14.59% from 2024-2032.
The Multichannel Campaign Management Market size was $5.14 Billion in 2023 and will reach $23.97 Billion by 2032 and grow at a CAGR of 18.66% by 2024-2032.
The Location Intelligence Market was valued at USD 19.3 billion in 2023 and is expected to reach USD 63.8 billion by 2032, growing at a CAGR of 14.23% by 2032.
Hybrid Cloud Market was valued at USD 96.78 billion in 2023 and is expected to reach USD 405.62 billion by 2032, growing at a CAGR of 17.31% by 2032.
The Virtual Networking Market was valued at USD 45.2 Billion in 2023 and is expected to reach USD 358.4 Billion by 2032, growing at a CAGR of 25.89% from 2024-2032.
Hi! Click one of our member below to chat on Phone