Get more information on Cybersecurity Market - Request Sample Report
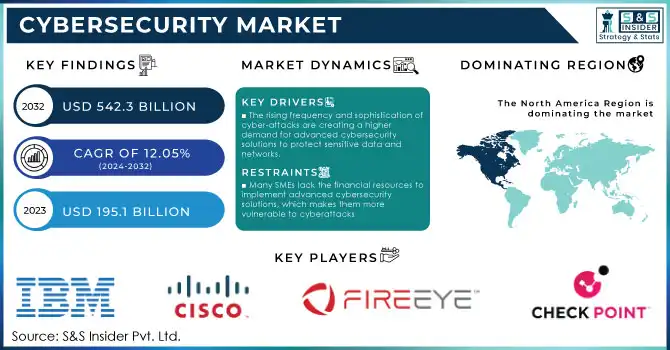
Cybersecurity Market was valued at USD 195.1 billion in 2023 and is expected to reach USD 542.3 Billion by 2032, growing at a CAGR of 12.05% from 2024-2032.
The cybersecurity market is growing swiftly, due to the rise in the number and complexity of cyber threats, and digital transformation occurring at a fast pace across sectors. The reason for this growth is the increasing demand for security solutions with cloud computing, IoT, and AI technologies. The dramatic rise in cyber-attacks and data breaches is one of the main drivers of this growth. This proves the utmost importance of a stricter security process, especially in finance, healthcare, and retail industries.
Market growth is further propelled by the rapid shift to remote work and cloud computing due to the COVID-19 pandemic. The shift of enterprises to the cloud has triggered a massive surge in demand for sophisticated Security solutions like multi-factor authentication, end-to-end encryption, and secure access service edge (sase) frameworks. Leading cloud providers such as Microsoft and Google are now embedding their platforms with advanced security functionalities to ensure that user data is well governed and meets compliance obligations such as the Rajon-General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA). Moreover, the rising sophistication of cybercrime and a rise in demand for sophisticated threat detection technologies have given rise to AI-based cybersecurity solutions. However, Palo Alto Networks reported that demand for its AI-based threat detection services rose 30% in 2023, illustrating the increasing need for reliance on AI services to proactively identify threats and respond to them. With organizations experiencing increased pressure to protect sensitive data, the market for cybersecurity solutions such as firewalls, intrusion detection systems (IDS), and endpoint security tools is rising. This trend is further driven by the increasing compliance requirements for regulatory compliance, which motivates organizations to utilize these advanced technologies for securing their digital assets and thus avoiding costly penalties.
|
Industry |
Company/Organization |
Cybersecurity Investment Focus |
|---|---|---|
|
Financial |
JP Morgan Chase |
$600 million annually on cybersecurity infrastructure |
|
Healthcare |
Anthem Inc. |
Increased investment in ransomware defense and patient data security |
|
Retail |
Walmart |
Strengthening e-commerce security through AI-driven fraud detection |
|
Technology |
|
Advanced cloud security and endpoint protection tools for cloud services |
Drivers
The rising frequency and sophistication of cyber-attacks are creating a higher demand for advanced cybersecurity solutions to protect sensitive data and networks.
High-profile data breaches and growing concerns over data privacy are propelling businesses to invest in robust security measures.
As businesses increasingly adopt digital technologies such as AI, IoT, and big data, the need for comprehensive cybersecurity solutions grows to safeguard complex infrastructures.
The rapid digitalization of businesses across sectors via technologies such as artificial intelligence (AI), the Internet of Things (IoT), and big data has resulted in such vastness and complexity of IT infrastructures, which consequently gives rise to an extensive need for swift, holistic cybersecurity. These technologies assist organizations with increased operational efficiency, improve user experiences, and be insightful from massive data. But, they also bring new security risks that need to be controlled to safeguard sensitive information and maintain business continuity.
For example, the automation of decision-making processes and the improvement of prediction capabilities brought by AI also has its benefits. However, it also introduces new security concerns such as algorithmic manipulation and adversarial attacks that can compromise system integrity. Likewise, the increase in Internet of Things (IoT) devices from consumer smart devices to industrial sensors is another factor widening the attack surface with more entry points available to cybercriminals. Most of these gadgets do not have solid warranties — which increases the risk of data breaches and cyber-attacks. The sudden growth of IoT, especially concerning healthcare, manufacturing, and logistics has paved the way for the need for specialty security solutions for these interconnected systems.
Big data has changed how industries operate, allowing organizations to make data-driven decisions based on a massive amount of data. Yet, the security challenges posed by BIG data are exacerbated by its volume and complexity, making it more attractive to criminals, and rendering huge amounts of data open to theft and ransom. Ensuring integrity, confidentiality, and compliance with big data (and stringent regulations like GDPR) are key motivators of investment dollars in next-gen cybersecurity solutions.
To tackle these enormous challenges, businesses are adopting all-in-one cybersecurity plans that incorporate AI-based threat detection, real-time monitoring, advanced encryption, and a safe cloud infrastructure. These solutions enable heightened management of the increasing complexity digital environments facilitate and a complex threat landscape. The cybersecurity market is growing in light of the increasing need for enhanced protection and regulatory compliance.
Restraints
Many SMEs lack the financial resources to implement advanced cybersecurity solutions, which makes them more vulnerable to cyberattacks
Organizations often face internal resistance to adopting new security technologies or shifting from legacy systems to more advanced cybersecurity solutions, delaying necessary upgrades
The sheer volume of security data generated can overwhelm security teams, leading to missed threats or delayed responses, reducing the effectiveness of security systems
Modern IT environments result in a substantial amount of security data, making it difficult for cybersecurity teams to manage trends. With tools such as firewalls, IDS, IPS, and endpoint protection solutions playing a vital role in detecting vulnerabilities and cyber threats, organizations realize they are generating an overwhelming amount of data in the form of logs, alerts, and traffic analysis. Consequently, it makes it difficult for the security analyst to prioritize alerts and often causes a threat to be missed or a delayed response. In addition to being resource-intensive, automated systems can create many alerts at once, most of which can be false positives, making it difficult for analysts to determine what cyber threats are in real time. The inability to address these alerts promptly leaves the systems open to attacks of ransomware, phishing, or data exfiltration, with studies showing that security teams do not have the bandwidth to investigate alerts immediately and that a delay in remediating attacks is possible.
The situation is further exacerbated by the rapid expansion of connected devices, networks, and cloud infrastructure, which adds complexity to the management of security data. Without the proper tools in place to aggregate and analyze data, detecting and responding to threats becomes a more challenging task. This is especially true for the small and medium-sized enterprises (SMEs) that do not have the resource base to implement solutions like Security Information and Event Management (SIEM) systems or AI-based threat detection tools as these can help reduce demands on data analysis resources by filtering through threats to focus on those that are critical.
By Organization Size
In 2023, the largest enterprise segment dominated the market and accounted for the highest share of revenue at 69.7%. Market drivers include large enterprise spending on IT infrastructure to enhance digital security to ensure the protection of large data storage. In addition, large enterprises have many servers, storage devices, endpoints & networks which can cause huge financial impacts due to cyber-attacks. Larger enterprises are focusing on the deployment of cyber security solutions to not only manage such issues but to secure the data fuelling the growth of the market.
The SME segment is projected to witness the fastest CAGR of 14.1% during the forecast period. SMEs are facing a greater challenge because of the pandemic, but their low-security postures make them more susceptible to attack, especially if cost savings have to be made. Also, their vacancy of security policies and worker skills additionally pulls them due to the very nature of a cyber-attack. Due to the aforementioned challenges, SMEs opt for cyber security insurance which shields them from financial losses from malicious software attacks and data breaches and aids the growth of this segment.
By Deployment
On-premises segment accounted for the largest market share of 62.8% in 2023 and will dominate the market over the forecast period. Complete ownership of the solutions by large enterprises ensures that the data is secure at an optimum level, due to the growing segment. In addition, on-premise security solutions further decrease the reliance on third-party companies surveying and securing data.
The cloud segment is expected to grow at a CAGR of 12.8% over the forecast period. This skyrocketing growth comes from migrating from the on-premises solutions of enterprises to the cloud. In addition, the cost and ease of deployment & management of cloud-based solutions are billowing the growth of this segment. Also, the reach for the solutions accessible over the devices in cloud technology is expected to create a lucrative opportunity for the growth of this segment.
By Component
The solutions segment dominated the market and represented a significant revenue share of 63.8%, with cyberattacks on the rise throughout recent years — from ransomware and phishing to data breaches — companies are spending a lot of money on proactive security. Cloud security solutions are in high demand because everyone is moving to the cloud so fast. As hybrid and multi-cloud environments rise, organizations are searching for solutions to protect and comply with data. As cyber threats become ever more sophisticated, so too will the solutions evolve; integrating AI and ML for faster detection and response capabilities. The specific market drivers are expected to continue to be driven by endpoint protection solutions and cloud security solutions considering the need for secure remote work. The increasing number of IoT devices also drives better protection will further lead to enable demand for integrated cybersecurity solutions.
The Services segment is expected to grow at the highest CAGR during the forecast period. Includes managed security services, incident response, security consulting, and training services. Organizations are struggling to fulfill the ever-evolving security needs, thanks to the rise in cyber threats and the explosion of complexity in IT environments. As a result, organizations use third-party specialized service providers for cyber security. The remote work boom, combined with more complex multi-cloud and hybrid environments, continues to drive demand for managed security services providers (MSSPs) for 24x7 monitoring, threat detection, and incident response. Increased demand for regulatory compliance — With the expansion of data protection laws like GDPR, HIPAA, etc., the need for regulatory compliance has never been higher, especially in sectors like healthcare, finance, and government, in turn increasing the demand for cybersecurity services.
Regional Analysis
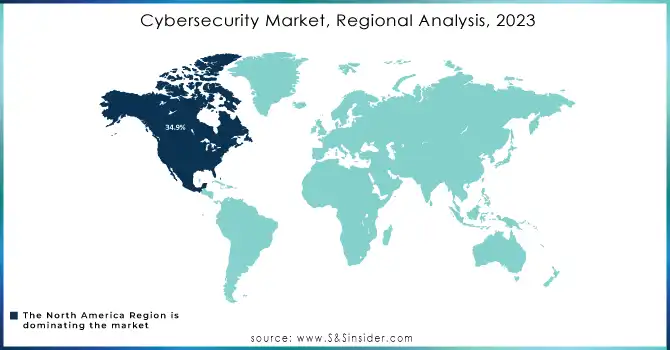
In 2022, North America dominated the market and accounted for the largest market share of 34.9%. North America's cyber security market is growing steadily as with some of the latest technologies it is been continued developed such as big data and the Internet of Things (IoT). In addition, the increasing number of IT companies and their diversified businesses in the region is prompting the requirement for endpoint device protection. In addition, governments around the world continue to pursue different initiatives to increase cyber security awareness in organizations and to promote and assist organizations to adopt sufficient cyber security measures. So, these above factors are going to drive the North American cyber security market.
Asia Pacific is projected to grow at the fastest CAGR throughout the forecast period. A growing number of data centers, increasing adoption of cloud technologies, growing cyber security jobs, and proliferation of IoT devices are attributing to the growth of the Asia Pacific cyber security market. In addition to this, various organizations in the Asia cyber security market solutions have inbuilt features to spot any possible weaknesses this is also shown as a supportive scenario for Asia Pacific cyber security market growth.
Need any customization research on Cybersecurity Market - Enquiry Now
Key Players
The major key players along with their products are
Cisco Systems - Cisco SecureX
Palo Alto Networks - Prisma Cloud
Check Point Software - Quantum Security Gateway
IBM Corporation - QRadar SIEM
Fortinet - FortiGate Firewall
McAfee - McAfee Endpoint Security
Symantec (Broadcom) - Symantec Endpoint Protection
Trend Micro - Trend Micro Apex One
Splunk - Splunk Enterprise Security
FireEye (Trellix) - Helix Security Platform
Sophos - Sophos Intercept X
CrowdStrike - CrowdStrike Falcon
Proofpoint - Proofpoint Email Protection
Forcepoint - Forcepoint DLP
Zscaler - Zscaler Internet Access
Okta - Okta Identity Management
Qualys - Qualys Cloud Platform
Bitdefender - Bitdefender GravityZone
Darktrace - Darktrace Cyber AI
Kaspersky Lab - Kaspersky Total Security
Recent Developments
January 2024: Palo Alto Networks Launched an AI-powered platform to automate threat detection and response for cloud-native environments
February 2024: CrowdStrike Introduced new endpoint detection capabilities with enhanced cloud integration to counter advanced persistent threats (APTs)
March 2024: Gem Security and Avalor both companies were acquired for $350 million each, focusing on threat detection and security analytics
| Report Attributes | Details |
| Market Size in 2023 | USD 195.1 billion |
| Market Size by 2032 | USD 542.3 Billion |
| CAGR | CAGR of 12.05% from 2024-2032. |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments |
• By Offering (Solution, Services) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles |
Cisco Systems, Palo Alto Networks, Check Point Software, IBM Corporation, Fortinet, McAfee, Symantec (Broadcom), Trend Micro, Splunk, FireEye, Sophos, CrowdStrike, Proofpoint, Forcepoint |
| Key Drivers | •The rising frequency and sophistication of cyber-attacks are creating a higher demand for advanced cybersecurity solutions to protect sensitive data and networks. •High-profile data breaches and growing concerns over data privacy are propelling businesses to invest in robust security measures. •As businesses increasingly adopt digital technologies such as AI, IoT, and big data, the need for comprehensive cybersecurity solutions grows to safeguard complex infrastructures. |
| Market Opportunities | •Many SMEs lack the financial resources to implement advanced cybersecurity solutions, which makes them more vulnerable to cyberattacks •Organizations often face internal resistance to adopting new security technologies or shifting from legacy systems to more advanced cybersecurity solutions, delaying necessary upgrades •The sheer volume of security data generated can overwhelm security teams, leading to missed threats or delayed responses, reducing the effectiveness of security systems |
Ans- Challenges in the Cybersecurity Market are
Ans- one main growth factor for the Cybersecurity Market is
Ans- the North America dominated the market and represented a significant revenue share in 2023
Ans- the CAGR of the Cybersecurity Market during the forecast period is 12.05% from 2024-2032.
Ans- Cybersecurity Market was valued at USD 195.1 billion in 2023 and is expected to reach USD 542.3 Billion by 2032, growing at a CAGR of 12.05% from 2024-2032.
Table of Contents:
1. Introduction
1.1 Market Definition
1.2 Scope (Inclusion and Exclusions)
1.3 Research Assumptions
2. Executive Summary
2.1 Market Overview
2.2 Regional Synopsis
2.3 Competitive Summary
3. Research Methodology
3.1 Top-Down Approach
3.2 Bottom-up Approach
3.3. Data Validation
3.4 Primary Interviews
4. Market Dynamics Impact Analysis
4.1 Market Driving Factors Analysis
4.1.1 Drivers
4.1.2 Restraints
4.1.3 Opportunities
4.1.4 Challenges
4.2 PESTLE Analysis
4.3 Porter’s Five Forces Model
5. Statistical Insights and Trends Reporting
5.1 Adoption Rates of Emerging Technologies
5.2 Network Infrastructure Expansion, by Region
5.3 Cybersecurity Incidents, by Region (2020-2023)
5.4 Cloud Services Usage, by Region
6. Competitive Landscape
6.1 List of Major Companies, By Region
6.2 Market Share Analysis, By Region
6.3 Product Benchmarking
6.3.1 Product specifications and features
6.3.2 Pricing
6.4 Strategic Initiatives
6.4.1 Marketing and promotional activities
6.4.2 Distribution and supply chain strategies
6.4.3 Expansion plans and new product launches
6.4.4 Strategic partnerships and collaborations
6.5 Technological Advancements
6.6 Market Positioning and Branding
7. Cybersecurity Market Segmentation, by Component
7.1 Chapter Overview
7.2 Solution
7.2.1 Solution Market Trends Analysis (2020-2032)
7.2.2 Solution Market Size Estimates and Forecasts to 2032 (USD Billion)
7.2.3 Firewall/Antimalware/Antivirus
7.2.3.1 Firewall/Antimalware/Antivirus Market Trends Analysis (2020-2032)
7.2.3.2 Firewall/Antimalware/Antivirus Market Size Estimates and Forecasts to 2032 (USD Billion)
7.2.4 Intrusion detection and prevention system (IDPS)
7.2.4.1 Intrusion detection and prevention system (IDPS) Market Trends Analysis (2020-2032)
7.2.4.2 Intrusion detection and prevention system (IDPS) Market Size Estimates and Forecasts to 2032 (USD Billion)
7.2.5 Identity and Access Management (IAM)
7.2.5.1 Identity and Access Management (IAM) Market Trends Analysis (2020-2032)
7.2.5.2 Identity and Access Management (IAM) Market Size Estimates and Forecasts to 2032 (USD Billion)
7.2.6 Data Loss Prevention (DLP) & Disaster Recovery
7.2.6.1 Data Loss Prevention (DLP) & Disaster Recovery Market Trends Analysis (2020-2032)
7.2.6.2 Data Loss Prevention (DLP) & Disaster Recovery Market Size Estimates and Forecasts to 2032 (USD Billion)
7.2.7 Security information and event management (SIEM)
7.2.7.1 Security information and event management (SIEM) Market Trends Analysis (2020-2032)
7.2.7.2 Security information and event management (SIEM) Market Size Estimates and Forecasts to 2032 (USD Billion)
7.2.8 Others (Encryption & Tokenization and Risk & Compliance)
7.2.8.1 Others (Encryption & Tokenization and Risk & Compliance) Market Trends Analysis (2020-2032)
7.2.8.2 Others (Encryption & Tokenization and Risk & Compliance) Market Size Estimates and Forecasts to 2032 (USD Billion)
7.3 Services
7.3.1 Services Market Trends Analysis (2020-2032)
7.3.2 Services Market Size Estimates and Forecasts to 2032 (USD Billion)
8. Cybersecurity Market Segmentation, By Deployment
8.1 Chapter Overview
8.2 On-premises
8.2.1 On-premises Market Trends Analysis (2020-2032)
8.2.2On-premises Market Size Estimates And Forecasts To 2032 (USD Billion)
8.3 Cloud
8.3.1 Cloud Market Trends Analysis (2020-2032)
8.3.2 Cloud Market Size Estimates And Forecasts To 2032 (USD Billion)
9. Cybersecurity Market Segmentation, By Security Type
9.1 Chapter Overview
9.2 Network Security
9.2.1 Network Security Market Trends Analysis (2020-2032)
9.2.2 Network Security Market Size Estimates And Forecasts To 2032 (USD Billion)
9.3 Cloud Application Security
9.3.1 Cloud Application Security Market Trends Analysis (2020-2032)
9.3.2 Cloud Application Security Market Size Estimates And Forecasts To 2032 (USD Billion)
9.4 End-point Security
9.4.1 End-point Security Market Trends Analysis (2020-2032)
9.4.2 End-point Security Market Size Estimates And Forecasts To 2032 (USD Billion)
9.5 Secure Web Gateway
9.5.1 Secure Web Gateway Market Trends Analysis (2020-2032)
9.5.2 Secure Web Gateway Market Size Estimates And Forecasts To 2032 (USD Billion)
9.6 Application Security
9.6.1 Application Security Market Trends Analysis (2020-2032)
9.6.2 Application Security Market Size Estimates And Forecasts To 2032 (USD Billion)
9.7 Others
9.7.1 Others Market Trends Analysis (2020-2032)
9.7.2 Others Market Size Estimates And Forecasts To 2032 (USD Billion)
10. Cybersecurity Market Segmentation, By Enterprise Size
10.1 Chapter Overview
10.2 Small & Medium Enterprises (SMEs)
10.2.1 Small & Medium Enterprises (SMEs) Market Trends Analysis (2020-2032)
10.2.2 Small & Medium Enterprises (SMEs) Market Size Estimates And Forecasts To 2032 (USD Billion)
10.3 Large Enterprises
10.3.1 Large Enterprises Market Trends Analysis (2020-2032)
10.3.2 Large Enterprises Market Size Estimates And Forecasts To 2032 (USD Billion)
11. Cybersecurity Market Segmentation, By Industry
11.1 Chapter Overview
11.2 BFSI
11.2.1 BFSI Market Trends Analysis (2020-2032)
11.2.2 BFSI Market Size Estimates And Forecasts To 2032 (USD Billion)
11.3 IT and Telecommunications
11.3.1 IT and Telecommunications Market Trends Analysis (2020-2032)
11.3.2 IT and Telecommunications Market Size Estimates And Forecasts To 2032 (USD Billion)
11.4 Retail
11.4.1 Retail Market Trends Analysis (2020-2032)
11.4.2 Retail Market Size Estimates And Forecasts To 2032 (USD Billion)
11.5 Healthcare
11.5.1 Healthcare Market Trends Analysis (2020-2032)
11.5.2 Healthcare Market Size Estimates And Forecasts To 2032 (USD Billion)
11.6 Government
11.6.1 Government Market Trends Analysis (2020-2032)
11.7.2 Government Market Size Estimates And Forecasts To 2032 (USD Billion)
11.7 Manufacturing
11.7.1 Manufacturing Market Trends Analysis (2020-2032)
11.7.2 Manufacturing Market Size Estimates And Forecasts To 2032 (USD Billion)
11.8 Travel and Transportation
11.8.1 Travel and Transportation Market Trends Analysis (2020-2032)
11.8.2 Travel and Transportation Market Size Estimates And Forecasts To 2032 (USD Billion)
11.9 Energy and Utilities
11.9.1 Energy and Utilities Market Trends Analysis (2020-2032)
11.9.2 Energy and Utilities Market Size Estimates And Forecasts To 2032 (USD Billion)
11.10 Others
11.10.1 Others Market Trends Analysis (2020-2032)
11.10.2 Others Market Size Estimates And Forecasts To 2032 (USD Billion)
12. Regional Analysis
12.1 Chapter Overview
12.2 North America
12.2.1 Trends Analysis
12.2.2 North America Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.2.3 North America Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.2.4 North America Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.5 North America Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.6 North America Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.7 North America Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.2.8 USA
12.2.8.1 USA Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.2.8.2 USA Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.8.3 USA Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.8.4 USA Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.8.5 USA Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.2.9 Canada
12.2.9.1 Canada Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.2.9.2 Canada Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.9.3 Canada Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.9.4 Canada Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.9.5 Canada Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.2.10 Mexico
12.2.10.1 Mexico Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.2.10.2 Mexico Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.2.10.3 Mexico Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.2.10.4 Mexico Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.2.10.5 Mexico Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3 Europe
12.3.1 Eastern Europe
12.3.1.1 Trends Analysis
12.3.1.2 Eastern Europe Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.3.1.3 Eastern Europe Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.1.4 Eastern Europe Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.5 Eastern Europe Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.6 Eastern Europe Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.7 Eastern Europe Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.1.8 Poland
12.3.1.8.1 Poland Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.1.8.2 Poland Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.8.3 Poland Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.8.4 Poland Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.8.5 Poland Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.1.9 Romania
12.3.1.9.1 Romania Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.1.9.2 Romania Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.9.3 Romania Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.9.4 Romania Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.9.5 Romania Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.1.10 Hungary
12.3.1.10.1 Hungary Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.1.10.2 Hungary Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.10.3 Hungary Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.10.4 Hungary Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.10.5 Hungary Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.1.11 Turkey
12.3.1.11.1 Turkey Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.1.11.2 Turkey Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.11.3 Turkey Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.11.4 Turkey Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.11.5 Turkey Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.1.12 Rest Of Eastern Europe
12.3.1.12.1 Rest Of Eastern Europe Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.1.12.2 Rest Of Eastern Europe Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.1.12.3 Rest Of Eastern Europe Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.1.12.4 Rest Of Eastern Europe Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.1.12.5 Rest Of Eastern Europe Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2 Western Europe
12.3.2.1 Trends Analysis
12.3.2.2 Western Europe Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.3.2.3 Western Europe Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.4 Western Europe Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.5 Western Europe Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.6 Western Europe Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.7 Western Europe Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.8 Germany
12.3.2.8.1 Germany Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.8.2 Germany Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.8.3 Germany Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.8.4 Germany Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.8.5 Germany Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.9 France
12.3.2.9.1 France Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.9.2 France Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.9.3 France Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.9.4 France Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.9.5 France Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.10 UK
12.3.2.10.1 UK Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.10.2 UK Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.10.3 UK Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.10.4 UK Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.10.5 UK Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.11 Italy
12.3.2.11.1 Italy Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.11.2 Italy Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.11.3 Italy Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.11.4 Italy Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.11.5 Italy Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.12 Spain
12.3.2.12.1 Spain Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.12.2 Spain Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.12.3 Spain Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.12.4 Spain Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.12.5 Spain Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.13 Netherlands
12.3.2.13.1 Netherlands Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.13.2 Netherlands Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.13.3 Netherlands Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.13.4 Netherlands Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.13.5 Netherlands Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.14 Switzerland
12.3.2.14.1 Switzerland Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.14.2 Switzerland Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.14.3 Switzerland Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.14.4 Switzerland Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.12.5 Switzerland Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.15 Austria
12.3.2.15.1 Austria Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.15.2 Austria Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.15.3 Austria Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.15.4 Austria Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.15.5 Austria Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.3.2.16 Rest Of Western Europe
12.3.2.16.1 Rest Of Western Europe Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.3.2.16.2 Rest Of Western Europe Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.3.2.16.3 Rest Of Western Europe Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.3.2.16.4 Rest Of Western Europe Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.3.2.16.5 Rest Of Western Europe Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4 Asia Pacific
12.4.1 Trends Analysis
12.4.2 Asia Pacific Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.4.3 Asia Pacific Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.4 Asia Pacific Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.5 Asia Pacific Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.6 Asia Pacific Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.7 Asia Pacific Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.8 China
12.4.8.1 China Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.8.2 China Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.8.3 China Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.8.4 China Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.8.5 China Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.9 India
12.4.9.1 India Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.9.2 India Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.9.3 India Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.9.4 India Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.9.5 India Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.10 Japan
12.4.10.1 Japan Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.10.2 Japan Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.10.3 Japan Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.10.4 Japan Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.10.5 Japan Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.11 South Korea
12.4.11.1 South Korea Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.11.2 South Korea Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.11.3 South Korea Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.11.4 South Korea Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.11.5 South Korea Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.12 Vietnam
12.4.12.1 Vietnam Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.12.2 Vietnam Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.12.3 Vietnam Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.12.4 Vietnam Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.12.5 Vietnam Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.13 Singapore
12.4.13.1 Singapore Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.13.2 Singapore Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.13.3 Singapore Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.13.4 Singapore Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.13.5 Singapore Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.14 Australia
12.4.14.1 Australia Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.14.2 Australia Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.14.3 Australia Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.14.4 Australia Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.14.5 Australia Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.4.15 Rest Of Asia Pacific
12.4.15.1 Rest Of Asia Pacific Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.4.15.2 Rest Of Asia Pacific Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.4.15.3 Rest Of Asia Pacific Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.4.15.4 Rest Of Asia Pacific Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.4.15.5 Rest Of Asia Pacific Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5 Middle East And Africa
12.5.1 Middle East
12.5.1.1 Trends Analysis
12.5.1.2 Middle East Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.5.1.3 Middle East Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.1.4 Middle East Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.5 Middle East Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.6 Middle East Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.7 Middle East Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.1.8 UAE
12.5.1.8.1 UAE Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.1.8.2 UAE Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.8.3 UAE Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.8.4 UAE Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.8.5 UAE Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.1.9 Egypt
12.5.1.9.1 Egypt Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.1.9.2 Egypt Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.9.3 Egypt Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.9.4 Egypt Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.9.5 Egypt Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.1.10 Saudi Arabia
12.5.1.10.1 Saudi Arabia Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.1.10.2 Saudi Arabia Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.10.3 Saudi Arabia Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.10.4 Saudi Arabia Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.10.5 Saudi Arabia Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.1.11 Qatar
12.5.1.11.1 Qatar Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.1.11.2 Qatar Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.11.3 Qatar Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.11.4 Qatar Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.11.5 Qatar Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.1.12 Rest Of Middle East
12.5.1.12.1 Rest Of Middle East Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.1.12.2 Rest Of Middle East Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.1.12.3 Rest Of Middle East Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.1.12.4 Rest Of Middle East Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.1.12.5 Rest Of Middle East Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.2 Africa
12.5.2.1 Trends Analysis
12.5.2.2 Africa Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.5.2.3 Africa Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.2.4 Africa Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.5 Africa Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.6 Africa Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.7 Africa Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.2.8 South Africa
12.5.2.8.1 South Africa Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.2.8.2 South Africa Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.8.3 South Africa Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.8.4 South Africa Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.8.5 South Africa Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.2.9 Nigeria
12.5.2.9.1 Nigeria Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.2.9.2 Nigeria Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.9.3 Nigeria Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.9.4 Nigeria Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.9.5 Nigeria Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.5.2.10 Rest Of Africa
12.5.2.10.1 Rest Of Africa Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.5.2.10.2 Rest Of Africa Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.5.2.10.3 Rest Of Africa Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.5.2.10.4 Rest Of Africa Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.5.2.10.5 Rest Of Africa Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.6 Latin America
12.6.1 Trends Analysis
12.6.2 Latin America Cybersecurity Market Estimates And Forecasts, By Country (2020-2032) (USD Billion)
12.6.3 Latin America Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.6.4 Latin America Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.5 Latin America Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.6 Latin America Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.7 Latin America Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.6.8 Brazil
12.6.8.1 Brazil Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.6.8.2 Brazil Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.8.3 Brazil Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.8.4 Brazil Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.8.5 Brazil Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.6.9 Argentina
12.6.9.1 Argentina Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.6.9.2 Argentina Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.9.3 Argentina Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.9.4 Argentina Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.9.5 Argentina Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.6.10 Colombia
12.6.10.1 Colombia Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.6.10.2 Colombia Cybersecurity Market Estimates And Forecasts, By Deployment (2020-2032) (USD Billion)
12.6.10.3 Colombia Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.10.4 Colombia Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.10.5 Colombia Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
12.6.11 Rest Of Latin America
12.6.11.1 Rest Of Latin America Cybersecurity Market Estimates And Forecasts, By Component (2020-2032) (USD Billion)
12.6.11.2 Rest Of Latin America Cybersecurity Market Estimates And Forecasts, Deployment (2020-2032) (USD Billion)
12.6.11.3 Rest Of Latin America Cybersecurity Market Estimates And Forecasts, By Security Type (2020-2032) (USD Billion)
12.6.11.4 Rest Of Latin America Cybersecurity Market Estimates And Forecasts, By Enterprise Size (2020-2032) (USD Billion)
12.6.11.5 Rest Of Latin America Cybersecurity Market Estimates And Forecasts, By Industry (2020-2032) (USD Billion)
13. Company Profiles
13.1 Cisco Systems
13.1.1 Company Overview
13.1.2 Financial
13.1.3 Products/ Services Offered
13.1.4 SWOT Analysis
13.2 Palo Alto Networks
13.2.1 Company Overview
13.2.2 Financial
13.2.3 Products/ Services Offered
13.2.4 SWOT Analysis
13.3Check Point Software
13.3.1 Company Overview
13.3.2 Financial
13.3.3 Products/ Services Offered
13.3.4 SWOT Analysis
13.4 IBM Corporation
13.4.1 Company Overview
13.4.2 Financial
13.4.3 Products/ Services Offered
13.4.4 SWOT Analysis
13.5 Fortinet
13.5.1 Company Overview
13.5.2 Financial
13.5.3 Products/ Services Offered
13.5.4 SWOT Analysis
13.6 McAfee
13.6.1 Company Overview
13.6.2 Financial
13.6.3 Products/ Services Offered
13.6.4 SWOT Analysis
13.7 Symantec (Broadcom)
13.7.1 Company Overview
13.7.2 Financial
13.7.3 Products/ Services Offered
13.7.4 SWOT Analysis
13.8 Trend Micro
13.8.1 Company Overview
13.8.2 Financial
13.8.3 Products/ Services Offered
13.8.4 SWOT Analysis
13.9 Splunk
13.9.1 Company Overview
13.9.2 Financial
13.9.3 Products/ Services Offered
13.9.4 SWOT Analysis
13.10 FireEye
13.10.1 Company Overview
13.10.2 Financial
13.10.3 Products/ Services Offered
13.10.4 SWOT Analysis
14. Use Cases and Best Practices
15. Conclusion
An accurate research report requires proper strategizing as well as implementation. There are multiple factors involved in the completion of good and accurate research report and selecting the best methodology to compete the research is the toughest part. Since the research reports we provide play a crucial role in any company’s decision-making process, therefore we at SNS Insider always believe that we should choose the best method which gives us results closer to reality. This allows us to reach at a stage wherein we can provide our clients best and accurate investment to output ratio.
Each report that we prepare takes a timeframe of 350-400 business hours for production. Starting from the selection of titles through a couple of in-depth brain storming session to the final QC process before uploading our titles on our website we dedicate around 350 working hours. The titles are selected based on their current market cap and the foreseen CAGR and growth.
The 5 steps process:
Step 1: Secondary Research:
Secondary Research or Desk Research is as the name suggests is a research process wherein, we collect data through the readily available information. In this process we use various paid and unpaid databases which our team has access to and gather data through the same. This includes examining of listed companies’ annual reports, Journals, SEC filling etc. Apart from this our team has access to various associations across the globe across different industries. Lastly, we have exchange relationships with various university as well as individual libraries.
Step 2: Primary Research
When we talk about primary research, it is a type of study in which the researchers collect relevant data samples directly, rather than relying on previously collected data. This type of research is focused on gaining content specific facts that can be sued to solve specific problems. Since the collected data is fresh and first hand therefore it makes the study more accurate and genuine.
We at SNS Insider have divided Primary Research into 2 parts.
Part 1 wherein we interview the KOLs of major players as well as the upcoming ones across various geographic regions. This allows us to have their view over the market scenario and acts as an important tool to come closer to the accurate market numbers. As many as 45 paid and unpaid primary interviews are taken from both the demand and supply side of the industry to make sure we land at an accurate judgement and analysis of the market.
This step involves the triangulation of data wherein our team analyses the interview transcripts, online survey responses and observation of on filed participants. The below mentioned chart should give a better understanding of the part 1 of the primary interview.
Part 2: In this part of primary research the data collected via secondary research and the part 1 of the primary research is validated with the interviews from individual consultants and subject matter experts.
Consultants are those set of people who have at least 12 years of experience and expertise within the industry whereas Subject Matter Experts are those with at least 15 years of experience behind their back within the same space. The data with the help of two main processes i.e., FGDs (Focused Group Discussions) and IDs (Individual Discussions). This gives us a 3rd party nonbiased primary view of the market scenario making it a more dependable one while collation of the data pointers.
Step 3: Data Bank Validation
Once all the information is collected via primary and secondary sources, we run that information for data validation. At our intelligence centre our research heads track a lot of information related to the market which includes the quarterly reports, the daily stock prices, and other relevant information. Our data bank server gets updated every fortnight and that is how the information which we collected using our primary and secondary information is revalidated in real time.

Step 4: QA/QC Process
After all the data collection and validation our team does a final level of quality check and quality assurance to get rid of any unwanted or undesired mistakes. This might include but not limited to getting rid of the any typos, duplication of numbers or missing of any important information. The people involved in this process include technical content writers, research heads and graphics people. Once this process is completed the title gets uploader on our platform for our clients to read it.
Step 5: Final QC/QA Process:
This is the last process and comes when the client has ordered the study. In this process a final QA/QC is done before the study is emailed to the client. Since we believe in giving our clients a good experience of our research studies, therefore, to make sure that we do not lack at our end in any way humanly possible we do a final round of quality check and then dispatch the study to the client.
Key Segments:
By Component
Solutions
Firewall/Antimalware/Antivirus
Intrusion detection and prevention system (IDPS)
Identity and Access Management (IAM)
Data Loss Prevention (DLP) & Disaster Recovery
Security information and event management (SIEM)
Others (Encryption & Tokenization and Risk & Compliance)
Services
By Deployment
On-premises
Cloud
By security Type
Network Security
Cloud Application Security
End-point Security
Secure Web Gateway
Application Security
Others
By Enterprise Size
Small & Medium Enterprises (SMEs)
Large Enterprises
By Industry
BFSI
IT and Telecommunications
Retail
Healthcare
Government
Manufacturing
Travel and Transportation
Energy and Utilities
Others
Request for Segment Customization as per your Business Requirement: Segment Customization Request
REGIONAL COVERAGE:
North America
US
Canada
Mexico
Europe
Eastern Europe
Poland
Romania
Hungary
Turkey
Rest of Eastern Europe
Western Europe
Germany
France
UK
Italy
Spain
Netherlands
Switzerland
Austria
Rest of Western Europe
Asia Pacific
China
India
Japan
South Korea
Vietnam
Singapore
Australia
Rest of Asia Pacific
Middle East & Africa
Middle East
UAE
Egypt
Saudi Arabia
Qatar
Rest of the Middle East
Africa
Nigeria
South Africa
Rest of Africa
Latin America
Brazil
Argentina
Colombia
Rest of Latin America
Request for Country Level Research Report: Country Level Customization Request
Available Customization
With the given market data, SNS Insider offers customization as per the company’s specific needs. The following customization options are available for the report:
Product Analysis
Criss-Cross segment analysis (e.g. Product X Application)
Product Matrix which gives a detailed comparison of product portfolio of each company
Geographic Analysis
Additional countries in any of the regions
Company Information
Detailed analysis and profiling of additional market players (Up to five)
The Privacy Management Software Market size was valued at USD 3.9 Billion in 2023 and will grow to USD 68.2 Billion by 2032 and grow at a CAGR of 37.4% by 2032.
IoT Middleware Market was valued at USD 15.4 billion in 2023 and is expected to reach USD 61.06 billion by 2032, growing at a CAGR of 16.58% by 2032.
The Endpoint Security Market Size was USD 17.7 billion in 2023 and is expected to reach USD 32.9 billion by 2032 and grow at a CAGR of 7.1% by 2024-2032.
The Virtual Event Platform Market size was USD 13.73 Billion in 2023 and is expected to reach USD 45.58 Billion by 2032 with a growing CAGR of 14.26% over the forecast period of 2024-2032.
Active Network Management Market was valued at USD 1.24 billion in 2023 and will reach USD 4.56 billion by 2032, growing at a CAGR of 15.64% by 2032.
5G Tester Market was valued at USD 3.45 billion in 2023 and is expected to reach USD 7.05 billion by 2032, growing at a CAGR of 8.29% from 2024-2032.
Hi! Click one of our member below to chat on Phone