Cloud Access Security Broker Market Report Scope:
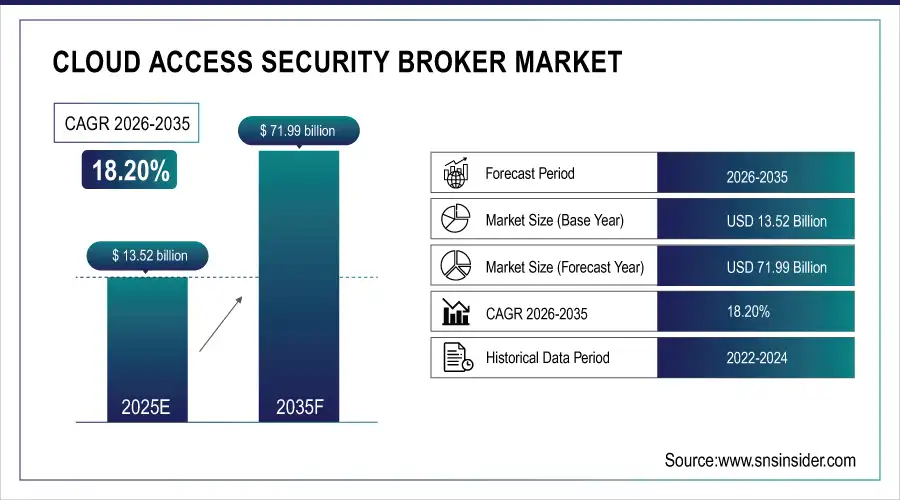
Cloud Access Security Broker Market was valued at USD 13.52 billion in 2025 and is expected to reach USD 71.99 billion by 2035, growing at a CAGR of 18.20% from 2026-2035.
The Cloud Access Security Broker market is witnessing remarkable growth as organizations increasingly adopt cloud-based services to enhance operational efficiency. This shift toward the cloud has heightened concerns about data security, compliance, and visibility, creating a strong demand for solutions that can address these challenges. CASBs fill this critical gap by offering tools for access control, user activity monitoring, and policy enforcement, which are essential in mitigating risks. Furthermore, the surge in cyber threats and the introduction of stringent regulatory frameworks, such as GDPR and CCPA, have further reinforced the need for robust CASB solutions.
Market Size and Forecast: 2025
-
Market Size in 2025 USD 3.58 Billion
-
Market Size by 2035 USD 19.52 Billion
-
CAGR of 23.6% From 2026 to 2035
-
Base Year 2025
-
Forecast Period 2026-2035
-
Historical Data 2022-2024
Get More Information on Cloud Access Security Broker Market - Request Sample Report
Cloud Access Security Broker Market Trends:
• Growing integration of CASB capabilities with zero trust and secure access service edge (SASE) architectures to enable unified cloud security management.
• Rising adoption of AI and machine learning within CASB platforms to improve threat detection, anomaly identification, and automated policy enforcement.
• Increasing demand for data loss prevention (DLP) and encryption features to meet stringent regulatory and compliance requirements.
• Expansion of CASB solutions to support multi-cloud and hybrid cloud environments used by large enterprises.
• Greater focus on user behavior analytics and real-time visibility to address risks from shadow IT and insider threats.
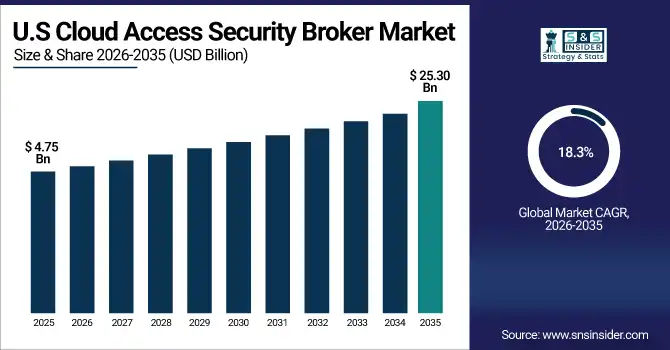
The U.S. Cloud Access Security Broker (CASB) Market is estimated to grow from USD 4.75 billion in 2025 to approximately USD 25.30 billion by 2035, registering a CAGR of about 18.3% during the forecast period. Growth is driven by strong enterprise cloud adoption, increasing cybersecurity threats, strict data protection regulations, and rising demand for visibility, compliance, and threat prevention across SaaS, IaaS, and PaaS environments.
Cloud Access Security Broker Market Growth Drivers:
-
Accelerating Cloud Migration Fuels Demand for Cloud Access Security Broker Solutions
As organizations increasingly transition to cloud environments, the need for robust security solutions grows. Businesses are leveraging cloud platforms for their scalability, cost-effectiveness, and ease of collaboration. However, this shift exposes them to potential security risks, such as data breaches, unauthorized access, and shadow IT. Cloud Access Security Brokers are pivotal in addressing these concerns, offering visibility, control, and protection over data stored and shared in the cloud. They enable enterprises to monitor and manage cloud usage, enforce security policies, and ensure compliance with regulations like GDPR, HIPAA, and others. As cloud adoption continues to rise across sectors, the role of CASBs in safeguarding sensitive information and mitigating threats becomes increasingly critical, driving their adoption in the market.
Cloud Access Security Broker Market Restraints:
-
High Implementation Costs Limit Cloud Access Security Broker Adoption Among SMEs
The high cost of deploying Cloud Access Security Brokers, including integration and ongoing maintenance, is a major factor deterring small and medium-sized enterprises from adopting these solutions. The initial investment required for implementation can be substantial, especially when considering additional cloud service costs. For example, AWS EC2 instances start at USD 0.0116 per hour, and S3 storage costs USD 0.023 per GB per month, while Google Cloud's Compute Engine instances begin at USD 0.0106 per hour, with storage costs from USD 0.020 per GB per month. Many SMEs struggle to allocate resources for both the setup and continuous updates. Beyond the upfront costs, businesses also face expenses related to training staff and ensuring that the solution integrates seamlessly with existing IT infrastructures. These financial challenges make it difficult for SMEs to justify the expenditure, especially when considering the return on investment.
Cloud Access Security Broker Market Segment Analysis:
BY APPLICATION
The Software as a Service segment dominated the Cloud Access Security Broker market in 2025, accounting for approximately 53% of the revenue share. This dominance can be attributed to the widespread adoption of SaaS applications across industries, driven by the need for scalable, flexible, and cost-effective solutions. As organizations increasingly rely on SaaS tools for collaboration, productivity, and business operations, the demand for CASBs to secure data and ensure compliance with regulatory requirements has grown significantly. The Platform as a Service segment is expected to grow at the fastest compound annual growth rate of 20.96% from 2026 to 2035. This rapid growth is fueled by the increasing demand for customizable cloud platforms that enable businesses to develop, run, and manage applications without the complexity of infrastructure management.
BY DEPLOYMENT
The Data Security segment led the Cloud Access Security Broker market in 2025, accounting for approximately 43% of the revenue share. This dominance is largely driven by the increasing need to protect sensitive data as organizations move to cloud environments. As businesses adopt cloud-based applications and store critical information online, securing data from breaches, unauthorized access, and cyberattacks has become a top priority, prompting widespread use of CASBs for enhanced data protection and compliance with industry regulations. The Risk and Compliance Management segment is poised to grow at the fastest compound annual growth rate of 20.23% from 2026 to 2035. This growth is fueled by the rising complexity of regulatory landscapes and the need for organizations to mitigate risks in increasingly distributed cloud environments.
By Enterprise Size
The Large Enterprises segment dominated the Cloud Access Security Broker market in 2025, capturing approximately 61% of the revenue share. This dominance is primarily due to the extensive reliance of large organizations on cloud-based services to manage vast amounts of data and streamline operations. With significant resources at their disposal, these enterprises are more equipped to invest in comprehensive security solutions, making data protection, regulatory compliance, and secure cloud adoption critical priorities. The Small and Medium-sized Enterprises segment is expected to grow at the fastest compound annual growth rate of 19.53% from 2026 to 2035. This growth is driven by the increasing cloud adoption among SMEs, which seek cost-effective, scalable, and secure cloud services without compromising on data security.

Cloud Access Security Broker Market Regional Analysis:
North America Cloud Access Security Broker Market Insights
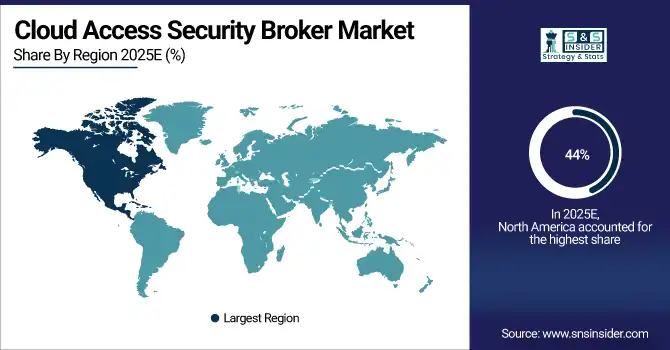
North America led the Cloud Access Security Broker market in 2025, accounting for approximately 44% of the revenue share. This dominance is largely attributed to the region's early adoption of cloud technologies, along with the presence of numerous large enterprises that require robust data security solutions. North American companies are at the forefront of digital transformation and cloud migration, driving demand for CASBs to ensure secure cloud access, compliance, and protection against evolving cyber threats.
Do You Need any Customization Research on Cloud Access Security Broker Market - Enquire Now
Asia Pacific Cloud Access Security Broker Market Insights
The Asia Pacific region is expected to grow at the fastest compound annual growth rate of 20.34% from 2026 to 2035. This rapid growth is fueled by the region's increasing cloud adoption across emerging markets, coupled with a heightened focus on cybersecurity due to the rise in cyber threats. As businesses in Asia Pacific expand their digital infrastructure, there is a growing need for CASBs to provide secure cloud access, mitigate risks, and comply with local and international data protection regulations, driving substantial market growth.
Europe Cloud Access Security Broker Market Insights
Europe’s CASB market is driven by strict data protection regulations such as GDPR, rising cloud adoption, and increasing cybersecurity threats. Enterprises across BFSI, healthcare, and government sectors are investing in CASB solutions to ensure compliance, data visibility, and secure cloud usage across SaaS and multi-cloud environments.
Latin America (LATAM) and Middle East & Africa (MEA) Cloud Access Security Broker Market Insights
The LATAM and MEA CASB market is growing as organizations accelerate cloud adoption and digital transformation. Rising awareness of data security, expanding SaaS usage, and strengthening regulatory frameworks are encouraging enterprises to adopt CASB solutions to protect sensitive data and manage cloud security risks.
Cloud Access Security Broker Market Key Players:
-
Skyhigh Networks (Skyhigh CASB, Skyhigh Secure SD-WAN)
-
Broadcom Inc. (Broadcom CASB, Symantec Cloud Security)
-
Palo Alto Networks Inc. (Prisma Cloud, Cortex XSOAR)
-
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
-
iboss Cybersecurity (iboss Cloud Security, iboss Zero Trust)
-
Netskope (Netskope Security Cloud, Netskope Private Access)
-
Lookout (Lookout CASB, Lookout Mobile Endpoint Security)
-
Zscaler, Inc. (Zscaler Internet Access, Zscaler Private Access)
-
Proofpoint Inc. (Proofpoint CASB, Proofpoint Email Security)
-
Microsoft Corporation (Microsoft Defender for Cloud, Microsoft Entra)
-
Bitglass, Inc. (Bitglass CASB, Bitglass Data Loss Prevention)
-
Censornet (Censornet Cloud Security, Censornet CASB)
-
Forcepoint (Forcepoint CASB, Forcepoint Data Loss Prevention)
-
McAfee, LLC (McAfee CASB, McAfee Web Protection)
-
Fortinet Inc. (FortiCASB, FortiGate Cloud)
-
Barracuda Networks Inc. (Barracuda Web Security, Barracuda CloudGen Firewall)
-
Trend Micro Inc. (Trend Micro Cloud App Security, Trend Micro Smart Protection)
-
IBM Corporation (IBM Cloud Security, IBM Security Identity Governance)
-
Thales Group (Thales Cloud Protection, Thales CipherTrust Cloud Key Manager)
-
Alert Logic Inc. (Alert Logic Cloud Security, Alert Logic Managed Detection)
-
CloudLock LLC (CloudLock CASB, CloudLock Cloud Security)
-
OneLogin Inc. (OneLogin CASB, OneLogin Identity Management)
-
CloudCodes Software Pvt. Ltd. (CloudCodes CASB, CloudCodes DLP)
-
CipherCloud Inc. (CipherCloud CASB, CipherCloud Data Encryption)
-
Oracle Corporation (Oracle CASB, Oracle Identity Cloud Service)
Competitive Landscape for Cloud Access Security Broker Market:
Skyhigh Security is a leading cloud security provider known for its Cloud Access Security Broker (CASB) platform, delivering comprehensive visibility, data protection, and threat prevention across SaaS, PaaS, and IaaS environments. Its CASB solution enables organizations to monitor cloud usage, enforce granular security policies, and protect against unauthorized access and data leakage, supporting secure cloud adoption and governance at scale
-
In October 2024, Skyhigh Security expanded its global cloud infrastructure, enhancing performance, security, and compliance across multiple regions. This growth supports its rapid customer adoption and strengthens its Security Service Edge solutions worldwide.
Broadcom Inc. offers its Symantec CloudSOC Cloud Access Security Broker (CASB) solution, providing enterprises with comprehensive visibility, data loss prevention, and threat protection across SaaS, IaaS, and multi-cloud environments. CloudSOC integrates with advanced DLP, user behavior analytics, and secure access technologies, helping organizations manage Shadow IT, enforce security policies, and ensure compliance with regulations. Broadcom’s integrated cloud security strategy leverages these capabilities to strengthen control and protection across cloud applications and reduce risks.
-
In August 2024, Broadcom unveiled VMware Tanzu Platform 10 at VMware Explore 2024, offering enhanced cloud-native application delivery and GenAI-powered intelligent app capabilities, accelerating software development for private cloud environments.
Microsoft’s Defender for Cloud Apps (formerly Cloud App Security) is a core CASB solution that delivers deep visibility, data protection, and threat detection across SaaS, PaaS, and IaaS environments. It integrates natively with Azure Active Directory and Microsoft 365, enabling cloud app discovery, granular policy enforcement, and compliance monitoring. The platform leverages rich analytics and automation to manage shadow IT, protect sensitive data, and enhance cloud security across both Microsoft and third-party applications.
-
In November 2024, Microsoft enhanced its Security Service Edge solution, introducing updates to Microsoft Entra Private and Internet Access, aimed at simplifying Zero Trust migrations, enhancing threat protection, and improving user access security with new integrations and capabilities.
|
Report Attributes |
Details |
|---|---|
| Market Size in 2025 | USD 13.52 Billion |
| Market Size by 2035 | USD 71.99 Billion |
| CAGR | CAGR of 18.20% From 2026 to 2035 |
| Base Year | 2025 |
| Forecast Period | 2026-2035 |
| Historical Data | 2022-2024 |
|
Report Scope & Coverage |
Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
|
Key Segments |
• By Solution (Control and Monitoring Cloud Services, Risk and Compliance Management, Data Security, Threat Protection, Others) |
|
Regional Analysis/Coverage |
North America (US, Canada), Europe (Germany, UK, France, Italy, Spain, Russia, Poland, Rest of Europe), Asia Pacific (China, India, Japan, South Korea, Australia, ASEAN Countries, Rest of Asia Pacific), Middle East & Africa (UAE, Saudi Arabia, Qatar, South Africa, Rest of Middle East & Africa), Latin America (Brazil, Argentina, Mexico, Colombia, Rest of Latin America). |
|
Company Profiles |
Skyhigh Networks, Broadcom Inc., Palo Alto Networks Inc., Cisco Systems, Inc., iboss Cybersecurity, Netskope, Lookout, Zscaler, Inc., Proofpoint Inc., Microsoft Corporation, Bitglass, Inc., Censornet, Forcepoint, McAfee, LLC, Fortinet Inc., Barracuda Networks Inc., Trend Micro Inc., IBM Corporation, Thales Group, Alert Logic Inc., CloudLock LLC, OneLogin Inc., CloudCodes Software Pvt. Ltd., CipherCloud Inc., Oracle Corporation |

