Automated Breach and Attack Simulation Market Size:
Get More Information on Automated Breach and Attack Simulation Market - Request Sample Report
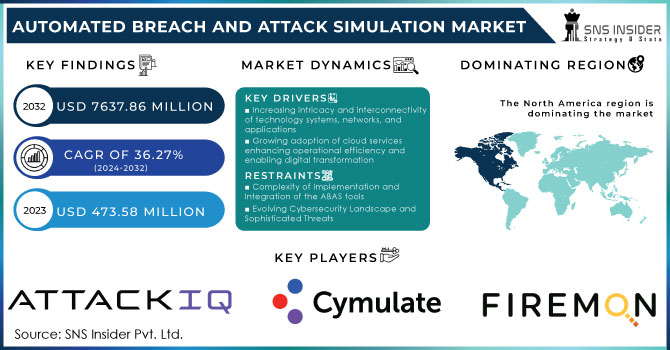
The Automated Breach and Attack Simulation Market size was valued at USD 473.58 million in 2023 and is expected to reach USD 7637.86 million by 2032 and grow at a CAGR of 36.27% over the forecast period 2024-2032.
The automated breach and attack simulation market (ABAS) is growing rapidly due to the increasing number of existing and potential cyber threats that encourage organizations to pay more attention to cybersecurity. The growing number of cyberattacks focused on ransom, phishing, and advanced persistent threats is one of the main drivers of the automated breach and attack simulation market. In 2023, about 57% of companies suffer from phishing attempts, and almost 3.4 billion daily malicious emails are detected, making up nearly 1.2% of all the sent e-mails. The financial losses are estimated to be $17,700 due to phishing scams in 2023.
While data breaches remain a major financial hurdle for organizations, as the average cost has reached a record high of USD 4.45 million in 2023, ransomware attacks cause even higher damage, averaging USD 5.13 million per incident. The country with the highest average cost of a breach is the United States, with USD 9.48 million, followed by the Middle East, which spends USD 8.07 million on average. Moreover, the methods used by the attackers also affect the costs, with phishing being the most expensive initial attack, costing organizations an average of USD 4.9 million per breach for attacks initiated through phishing emails. Finally, breaches of entities with poor compliance practices cost more, with the average being USD 5.05 million in 2023. Therefore, ABAS solutions are highly important because they allow organizations to determine vulnerabilities and test the existing security tools under real-world cyberattack simulation.
Market Dynamics
Drivers
-
Increasing intricacy and interconnectivity of technology systems, networks, and applications
IT in the modern world is becoming more complex, and organizations often choose several technology solutions like cloud computing, the use of the Internet of Things, and even mobile applications. However, the complexity of their frequent use complicates providing their security, as the traditional approaches to safety do not work in many respects. ABAS tools refer to automated types of security applications and highlight this type of service among other applications for their continuous testing, which determines their advantages in the protection of the growing IT power. Automated BAS tools can simulate adversary actions against various layers of IT, including networks, applications, devices, and even the cloud system. This ability appears to be a benefit due to protection testing for any possible action. Together with this, the test will identify all detectable vulnerabilities, which, in turn, allows for ensuring continuous implementation across the entire attacked surface. The same advantages are related to the use of this type of protection for the annual exhibition area environment, but the automated variant performs better due to its ability to change along with actions.
-
Growing adoption of cloud services enhancing operational efficiency and enabling digital transformation
Cloud computing services have gained widespread acceptance over the years, driving significant changes to the IT environment of organizations by providing them with scalable, flexible, and low-cost systems to match their needs. The global IT industry has been heavily affected by the rapid adoption of cloud computing services, becoming a truly groundbreaking side of today’s IT environment. These services provide companies with scalable, flexible, and easily manageable solutions. In 2023, the number of cloud intrusions has increased by 75%, whereas the cases of compromised cloud data have grown by 110%. Automated BAS tools may help in continuously validating and testing cloud security. Zero trust security is a security framework that is different from the traditional where everything inside the network perimeter is trusted. ABAS tools are essential for testing and validating zero-trust environments and ensuring that they run securely. Such requirements have already been introduced in 24% of companies in 2023, which proves the relevance of such a proactive approach to cyber security.
Restraints
-
Complexity of Implementation and Integration of the ABAS tools
Implementing automated BAS solutions is a complicated and labor-intensive task that becomes one of the leading restraints for clients. The problems are evident both for small organizations and global corporations with complicated and big IT settings. The most significant difficulty is that automated BAS has to be included in the general security system, which consists of security policies, devices, and security specialists. From the system perspective, the BAS tool has to become a part of the particular SIEM platform, which combines data from firewalls, IDS, and other tools. This reflects the whole complexity and the number of different tasks that BAS tools have to solve. At the same time, the complex implementation procedure also hinders the adoption rate, as many organizations do not have professionals to complete Automated BAS solution deployment.
-
The evolving cybersecurity threat landscape continuously changing and an increasingly sophisticated array of cyber threats
The threat landscape in cybersecurity is not still and continues to evolve with time. As such, new attack methods are being developed commonly and frequently. Moreover, since the threat landscape is continuously changing, so are the tools that should be able to simulate and arrange these threats change. Hence, the development and maintenance of these tools are directly tied to the rate of development and the appearance of new threats. This implies that monitoring the new and changing threat landscape and adjusting these automated BAS tools is a costly affair. A potential solution is to use AI and ML for developing the Automated BAS solutions. With regular and updated data, AI and ML can be easily developed to identify the threats that are new or emerging and automatically simulate these attacks.
Market Segmentation
By Deployment
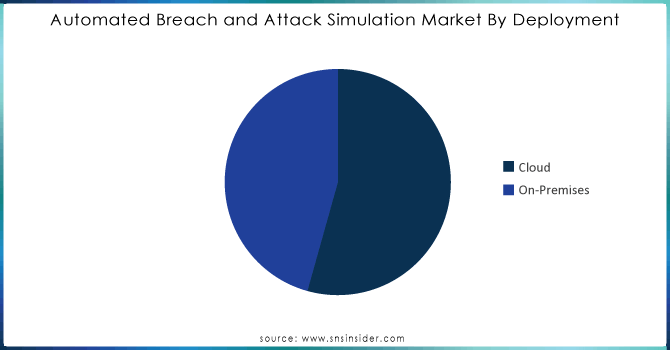
The cloud segment accounted for the largest market share of 54.35% in 2023. Up to 94% of malware is delivered to organizations via email which increases the demand for BAS to simulate the use of this type of commonly used attack vector. The service is used to simulate cyberattacks on an enterprise’s cloud environment on an ongoing basis, allowing the system’s weaknesses to be identified, and the effectiveness of security controls to be proven. The implementation of the service in the form of a cloud-based one makes it scalable and flexible, and, therefore, such a system can be applied by both small and large businesses.
The on-premises segment has a CAGR rate of 36.66% during the forecast period 2024-2032. Security testing might be entirely within an organization’s infrastructure, especially those working in highly regulated industries like healthcare sectors. In February 2024, a ransomware attack was launched on United States health-owned technology company Change Healthcare. A new cybersecurity program has been unveiled by the United States Department of Health and Human Services (HHS) agency to better protect hospitals amid the rising cyber threats affecting the health sector and disrupting patient care. The Advanced Research Projects Agency for Health decided to invest more than $50 million to develop a suite of software that could automatically scan the model hospital environments looking for potential vulnerabilities that hackers might target and come up with solutions as fast as possible to fix it.
Need any customization research on Automated Breach and Attack Simulation Market - Enquiry Now
By Offering
The platform and tools segment dominated the market with a market share of over 62.89% in 2023. The growth is driven by the ease of tools’ implementation into the existing framework. Smooth implementation of various platforms and tools improves their security setting without switching to an entirely new infrastructure and makes the usage of automated breach and attack simulation tools more appealing. For example, AttackIQ is a leader in BAS technologies, and its full-stack platform includes a library of pre-built attack simulations and gives one the ability to create custom attacks.
The services segment is the fastest-growing with a CAGR of 36.67% during the forecast period 2024-2032. The lack of the in-house needed expertise or resources represents a problem for security testing with the periodicity required to properly protect companies, especially SMBs. In 2023, 41% of small businesses were hit by ransomware, which is nearly double the 22% observed in 2021. Further, 95% of SMB incidents in cybersecurity cost firms from $826 to $653,587. Lastly, in the past 12 months, US small and mid businesses have paid over $16,000 in cyber ransoms. The service providers can fill in the gap and they are known for scalable and affordable solutions that can make regular simulations.
By Application
The configured management segment led the market and accounted for a share of 36.02% in 2023. Configuration management tools are software that enhances the stability and agility of a system. They are designed to automate the management and tracking of IT infrastructure. It assists DevOps teams by automating the provisioning, configuration, and deployment of software and hardware resources across diverse environments. For Instance, Puppet Enterprise delivers the tools businesses need to manage secure infrastructure more efficiently at the scale of secure solutions through its agent-based automation.
The patch management segment is expected to grow at a CAGR of 36.90% during 2024-2032. According to Microsoft, 80% of cyberattacks happen because of unpatched software vulnerabilities. From a survey of 500 organizations, 75% of them think that they are vulnerable to any cyber-attacks because of the unpatched software they are using now. Patch management applications of automated breach and attack simulation tools continue to be used by organizations to ensure that all devices are updated with the necessary security patches at all times.
By End User
The enterprises and data centers segment held a market share of over 61.29% in 2023. The creation of new tools and increasingly complicated threats determine a more proactive approach to identifying vulnerabilities that can be exploited by cybercriminals. The total breaches triggered by the ransomware attack reduced by 41% in 2023. It is still important to improve approaches and implement special practices with the help of which the number of cases might be this small.
The managed service providers segment is expected to grow at 36.73% CAGR during the forecast period. These providers are responsible for the overall management of multiple client organizations’ IT infrastructure and the security of this infrastructure. The reliance of different entities on the managed service providers increases sales and requests for the implementation of testing mechanisms to ensure the overall reliability of defense.
Regional Analysis
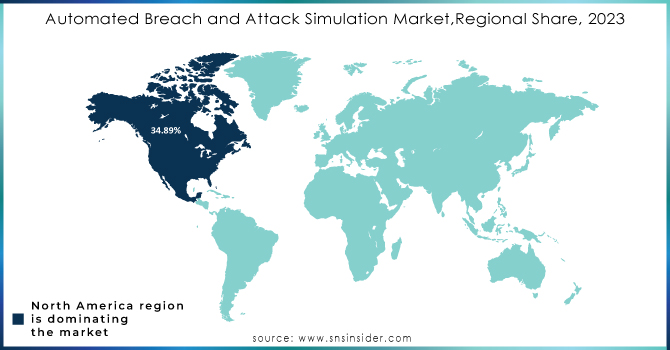
North America held the major share of over 34.89% in 2023 and dominates the market. Better awareness about cybersecurity risks among regional enterprises is driving the growth of the market across the region, especially the U.S. is showing substantial market growth. The increasing complexity of the IT environment is the major driving factor influencing the growth of the market in the U.S. In 2023, around 100+ cases were filed in the U.S. for data breaches in top IT companies, which has consequently affected around 15 million people. ABAS tools aim at continuous and automated testing of all the security controls across the diverse IT environments of enterprises to identify and fix the actual security vulnerabilities in real-time.
Asia Pacific is expected to grow fast at a CAGR of 36.70% in the forecast period 2024-2032. System intrusion, social engineering, and basic web application attacks represent 95% of breaches in APAC. As the number of cyberattacks rises, the vital economic sectors of Asia become more susceptible to the threat. The most frequent victims of cyberattacks included government agencies, industrial, and IT companies, and financial institutions. Out of the mentioned organizations, government agencies were the most affected, as they were targeted in 22% of the total. Moreover, the emergence of SMEs across the region is also augmenting the growth of the market, as SMEs are now implementing feasible automated breach and attack simulation tools to safeguard their digital assets and customer data from evolving cyber risks.
Key Players
The major market players are AttackIQ, Cymulate, IronNet Inc., CronusCyber.Com, FireMon LLC, Keysight Technologies, Mandiant, Qualys Inc., Rapid7, Scythe, ReliaQuest LLC, SafeBreach Inc., Sophos Inc., XM Cyber, Skybox Security Inc., Verodin, NopSec, CyCognito, Aujas, BitDam, Phoenix Datacom, Picus Security, Balbis, GuardiCore, and others.
Recent Development
-
Picus Security (December 2023): Launched a new channel partner program to simplify partnerships with VARs and help MSSPs add a differentiating offering to their lineups.
-
Skyhawk Security (May 2024): Unveiled a cloud-native Continuous Threat Exposure Management (CTEM) solution, empowering organizations to automate their CTEM program and operationalize it through the AI-based Synthesis Security Platform.
-
AttackIQ (March 2024): Announced AttackIQ Ready! 2.0, a managed breach and attack simulation-as-a-service combining fully automated and on-demand adversary emulation testing.
| Report Attributes | Details |
|---|---|
| Market Size in 2023 | USD 473.58 million |
| Market Size by 2032 | USD 7637.86 million |
| CAGR | CAGR of 36.27% From 2024 to 2032 |
| Base Year | 2023 |
| Forecast Period | 2024-2032 |
| Historical Data | 2020-2022 |
| Report Scope & Coverage | Market Size, Segments Analysis, Competitive Landscape, Regional Analysis, DROC & SWOT Analysis, Forecast Outlook |
| Key Segments | • By Deployment (Cloud, On-premises) • By Offering (Platforms & Tools, Services) • By End User (Configured, Patch, Threat, Others) • By Application (Enterprises & Data Centers, Managed Service Provider) |
| Regional Analysis/Coverage | North America (US, Canada, Mexico), Europe (Eastern Europe [Poland, Romania, Hungary, Turkey, Rest of Eastern Europe] Western Europe] Germany, France, UK, Italy, Spain, Netherlands, Switzerland, Austria, Rest of Western Europe]), Asia Pacific (China, India, Japan, South Korea, Vietnam, Singapore, Australia, Rest of Asia Pacific), Middle East & Africa (Middle East [UAE, Egypt, Saudi Arabia, Qatar, Rest of Middle East], Africa [Nigeria, South Africa, Rest of Africa], Latin America (Brazil, Argentina, Colombia, Rest of Latin America) |
| Company Profiles | AttackIQ, Cymulate, IronNet Inc., CronusCyber.Com, FireMon LLC, Keysight Technologies, Mandiant, Qualys Inc., Rapid7, Scythe, ReliaQuest LLC, SafeBreach Inc., Sophos Inc., XM Cyber, Skybox Security Inc., Verodin, NopSec, CyCognito, Aujas, BitDam, Phoenix Datacom, Picus Security, Balbis, GuardiCore |
| Key Drivers | • Increasing intricacy and interconnectivity of technology systems, networks, and applications • Growing adoption of cloud services enhancing operational efficiency and enabling digital transformation |
| RESTRAINTS | • Complexity of Implementation and Integration of the ABAS tools • The evolving cybersecurity threat landscape continuously changing and an increasingly sophisticated array of cyber threats |

